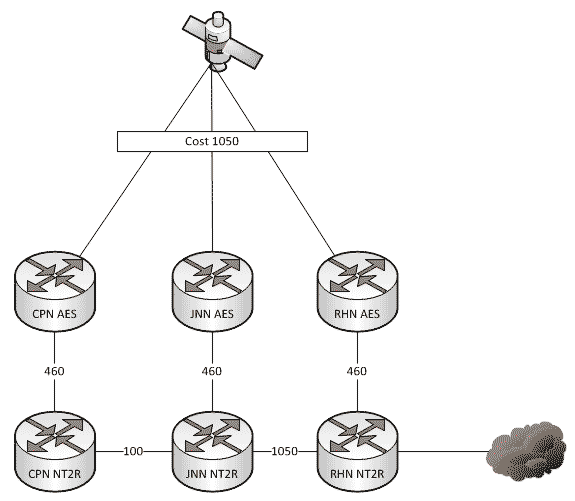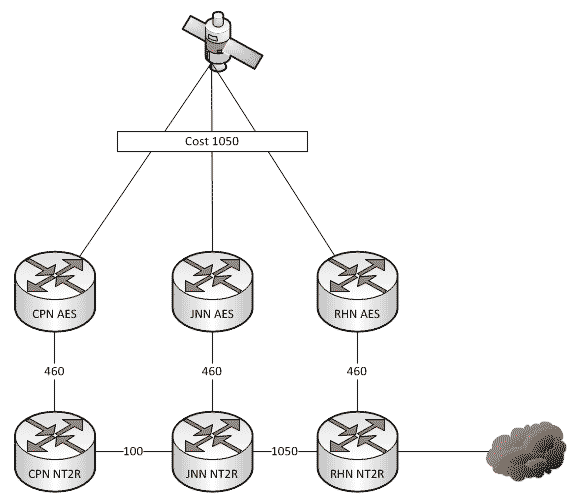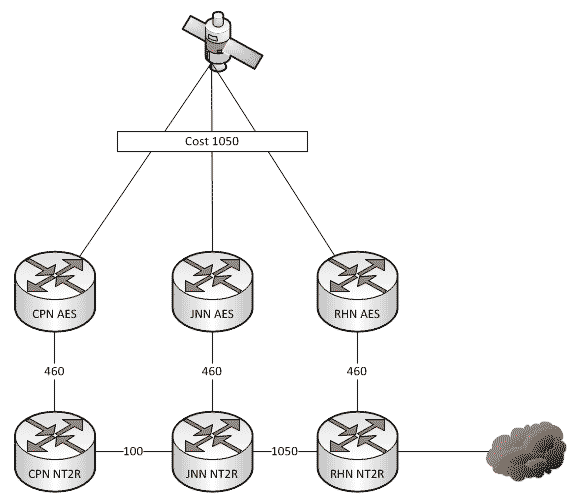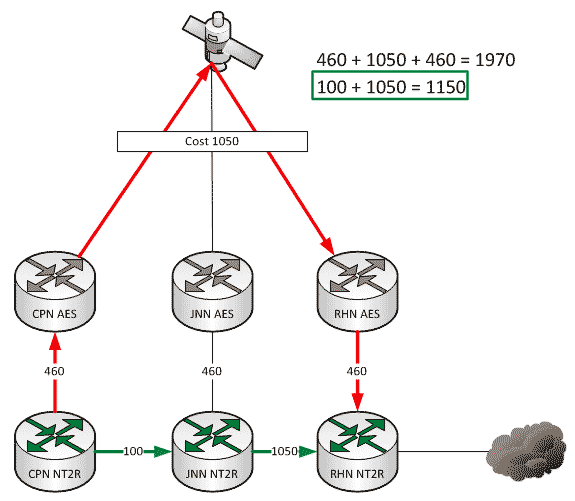
As a general rule, all WIN-T nodes route traffic in pretty much the same way using pretty much the same configuration. We all know that at a CPN, both SIPR and NIPR traffic goes out the nodes TDMA link because, well, it has no other way to go. For a JNN, if the traffic is going to one of our subordinate units it goes out our TDMA, and if it is going somewhere else, it likely goes out our FDMA. We understand what it does, but most people have stopped thinking about why it does that. This is fine and dandy until we start making changes to the network.
Protecting Printers
The Army, and the world in general, has been slow to accept the fact that anything on a network can present a risk to that network. Routinely, we’ll place a device on the network without properly configuring it, patching it, or securing it without a second thought. Even on the occasion that we do think about the security of that device, we look at the device as being unimportant and it doesn’t really matter if it is compromised. Today we’ll talk about the threat sitting in the corner of the TOC….the printer
Management of the Network on the Fly
You just rolled onto your new site after a 5 hour convoy which was delayed 2 hours already. You haven’t been able to see the network for nearly 9 hours and it will be a couple more before you have minimal connectivity in the Main. So, what does your network look like?
Orders, Suggestions, and Good Ideas
Have you ever told a unit that you needed them to do something, only for them to completely blow you off? Since its formation, the Army has operated under as an organization of order. We as warrant officers have to learn to utilize the orders process to enable us to successfully manage the network.