This is the first of what will hopefully be many walk-throughs from various CTF competitions I’ve competed/worked on. This first challenge is a simple one that I created for the 5th annual Army Cyber Skills Challenge.
Problem
Note: This challenge is set in a scene from the book “Ready Player One” which is actually a pretty cool read. I highly recommend it.
Innovative Online Industries (IOI) is trying to figure out where Wade lives so that they can make him an offer he can’t refuse. Unfortunately, the only real clue that they currently have is this photo that he posted on his profile. What street does he live on?
Note: Enter the flag as acsc2017{}. Do not include the road description (rd, st, dr, etc)
Not sure what changes WordPress makes to the file, so here is a direct link to the image.

Solution
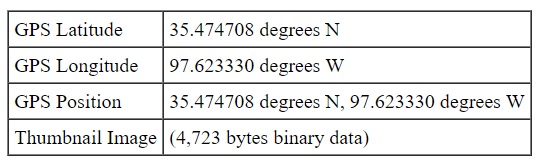
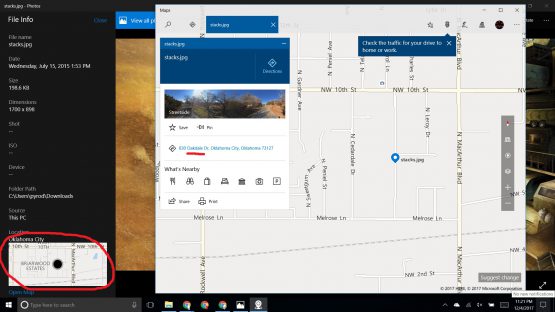
So this is a pretty easy problem. Most images today have a lot more information embedded in them besides just the image itself. Exif data is a type of metadata that contains image specific information such as details about the camera that took it, the programs that edited it, and in this case the GPS location of where the image was taken. When I created the challenge, I did it on my Centos box which shows the raw lat/long of the image that you then had to take and put into Google Maps. I didn’t realize it at the time, but Windows 10 makes it even easier. When you open the image and bring up the file info, it shows you right on the map where it is. Either way, if you look on the map, you see that the lat/long given (35.474708 degrees N, 97.623330 degrees W) will put you outside of Oklahoma City on a street called Oakdale, meaning that the flag was acsc2017{Oakdale}.