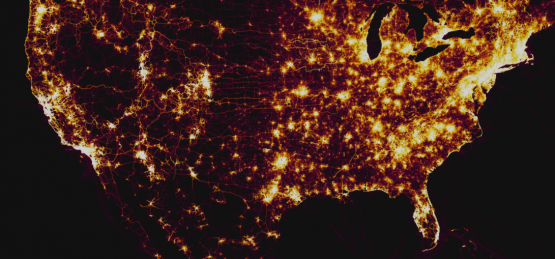
I am in Augusta for the next few weeks for the ARCYBER Work Role Working Group (WRWG) and some training. While I was waiting for my plane yesterday, I came across a story in my news feed talking about how publicly available GPS data may have exposed the location of classified US bases overseas. In November of last year, Strava, a fitness app that among other things uses GPS data to track your workout, released a heat map of over a billion data points showing where it’s users were working out. The picture to the right shows an overall shot of the US. No real surprises where there are huge concentrations of people who work out but after looking at the map recently, Nathan Ruser (@Nrg8000) noticed that he could very easily zoom in and identify the locations of US bases in Iraq and Syria among other places. Looking further, he also found what he suspects are US bases that aren’t publicly known. For obvious reasons, I won’t point out those locations but as an example lets look at a place I am very familiar with…Fort Irwin, CA.
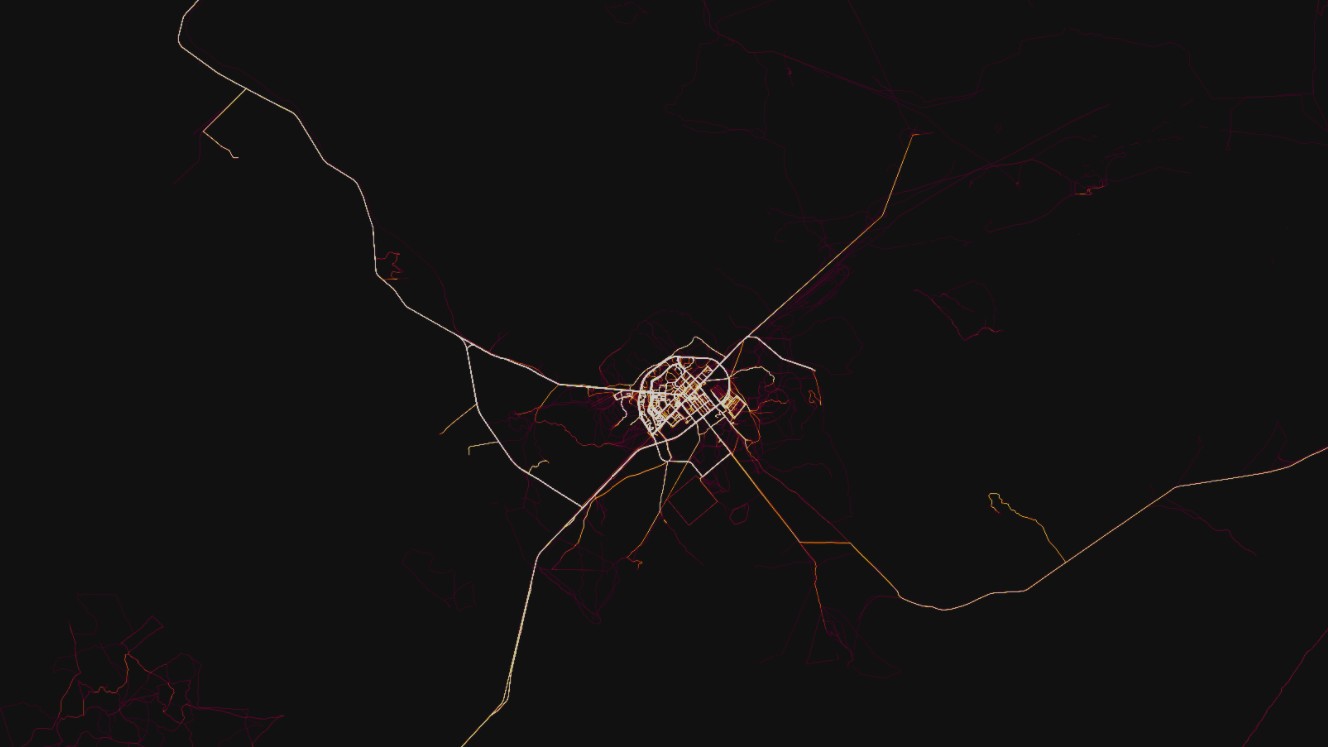
Here is an overall shot of Fort Irwin. You can clearly identify Irwin Rd which brings you onto base from Barstow, as well as the main loop around the cantonment area. You can see Goldstone road (the road I loved to run my 2 miles on, as well as Bullrun (another popular running route). But looking outside of the main area of the base, you see FOB Santa Fe, including the path that a countless number of poor souls had to walk as the guarded the perimeter of the FOB. Moving around a little more, you see a clear path leading up to OP2, a popular retrans location as well as Porta Poti Wadi, another popular retrans location.
 Many people believe that just because they aren’t “working out”, that they Fitbit or other fitness device on their wrist isn’t keeping track of where they are, but this clearly shows otherwise. The device is always tracking where you are. When you’re working out, when you’re walking, and even when you’re driving. Now clearly, in this particular example, the data isn’t live (it was aggregated over the course of 2 years) and it doesn’t tie back to a particular person, but it’s not that hard to do. I personally use a fitness tracker on my bike when I go for a ride which posts my route as soon as I am done. That is real location information, that is only an hour or two old, and it’s pretty easy to come across if you’re looking in a general area.
Many people believe that just because they aren’t “working out”, that they Fitbit or other fitness device on their wrist isn’t keeping track of where they are, but this clearly shows otherwise. The device is always tracking where you are. When you’re working out, when you’re walking, and even when you’re driving. Now clearly, in this particular example, the data isn’t live (it was aggregated over the course of 2 years) and it doesn’t tie back to a particular person, but it’s not that hard to do. I personally use a fitness tracker on my bike when I go for a ride which posts my route as soon as I am done. That is real location information, that is only an hour or two old, and it’s pretty easy to come across if you’re looking in a general area.
This is not the first time that GPS data has gotten the military (both our’s and others) in trouble over the years. I remember not long after I got into Iraq for the first time in 2004, there was a lot of talk around the base about using personal handheld radios around the FOB or on convoys. Not only were the radios not encrypted, but in some cases, they would transmit your GPS location in the clear every time you talked allowing anyone who was within range to get your location.
In 2014, Russian forces deployed across the boarder and took control of Crimea region of eastern Ukraine. While most of the world knew that they were there, the Russians repeatedly denied it. Then one day a poor Soldier who “wasn’t in Ukraine” posted a picture of himself on Instagram. Unfortunately for him, the picture had the GPS location embedded in it, and he had decided to previously share the location of his pictures. When he took his picture, it popped up on the map and clearly showed him sitting in Ukraine.
So what do we do? For the vast majority of us, wearing a fitness tracker is not a big deal. It is no secret where Fort Meade or Fort Hood or Fort Whatever is located. Overseas, the vast majority of our bases are publicly known as well. That being said, when you go somewhere that you can’t tell your family where you are, you should probably leave the fitness tracker at home. If you are going out on a patrol, you should probably leave the fitness tracker in your CHU. Bottom line, realize that we are continually feeding a number of organizations our location. If that is a problem, make sure you’re not doing it.



What’s the purpose/goal of this WRWG?
Defining work roles and requirements for the cyber force.
17CMF specifically? or 255S, etc included?
all cyber work roles
I’m in the S course now, which is why that peaked my interest. Thanks
It affects the 255S that are working in cyber roles (NMT, NST, CMT, CST, etc), not the ones that are still working signal roles.
I lol’d when I read that article last night on the Satcom page. OPSEC baby – it’s how we knew the Russians were in Georgia – Geotagging
So a (now retired) LTC I know was on a tour overseas with USASOC. He posted a picture of a football team flag in the desert…..Facebook posted where he was at.
We may or may not have confirmed or denied that we were operating in that area. Many people had to blast him to change his settings.
When you start seeing these locations pop up in the middle of the ocean where there are no islands you know you have a problem lol.
Soldiers have been geo-tagging since Geocaches were being strewn across FOBs in the mid-2000s and Garmin devices – all public, just not highlighted.
If this came to light years ago…..why was it not fixed?