Another problem from ACSC5. You can find it here.
Problem
You’ve been able to get on a router and capture some traffic in an effort to map out the the corporate network. Your intelligence team has told you that your target device has an IP address of 172.16.58.47 but no one knows that actual location of it. Examine the network traffic and see if you can figure out the location of that device.
NOTE: I screwed up and used the format ACSC{} when I put this together and didn’t have time to recreate it all
Solution
This one was actually a lot of fun to build but I was surprised how many people took it in a direction I wasn’t expecting when they tried to solve it. Download the PCAP file and open it up in Wireshark. As noted in the problem description, I screwed up the flag format and didn’t get to fix it so the flag we are looking for is ACSC{}. The first thing that almost everyone did was do a simple search for the flag format. Fortunately I thought of that, and put in fake flags so you couldn’t do it that easily.
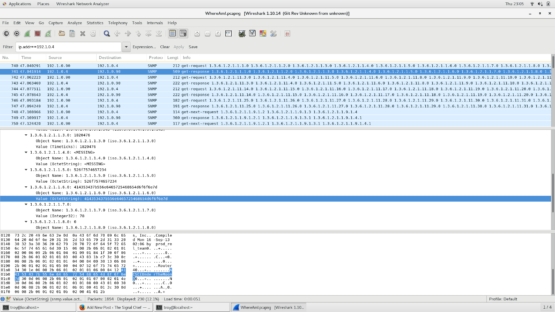
 There are a few steps to solving this one. The only thing we are really given is an IP address of 172.16.58.47. If you sort the packet capture by source or destination IP address, you’ll see that that address doesn’t show up anywhere. If you try and do a simple search for the IP address, it doesn’t show up. Looking at the capture you see a lot of OSPF traffic. Implement a BPF of just “ospf” so you can look at the packets. The field we are looking at specifically is “Source OSPF Router” in the OSPF header. This is the router ID for the router for the router advertising the networks in that packet. If you go down to packet 10, you see the pictured packet below with a Router ID of 172.16.58.47. Looking at the actual IP address of the packet itself and we see 192.1.0.4.
There are a few steps to solving this one. The only thing we are really given is an IP address of 172.16.58.47. If you sort the packet capture by source or destination IP address, you’ll see that that address doesn’t show up anywhere. If you try and do a simple search for the IP address, it doesn’t show up. Looking at the capture you see a lot of OSPF traffic. Implement a BPF of just “ospf” so you can look at the packets. The field we are looking at specifically is “Source OSPF Router” in the OSPF header. This is the router ID for the router for the router advertising the networks in that packet. If you go down to packet 10, you see the pictured packet below with a Router ID of 172.16.58.47. Looking at the actual IP address of the packet itself and we see 192.1.0.4.
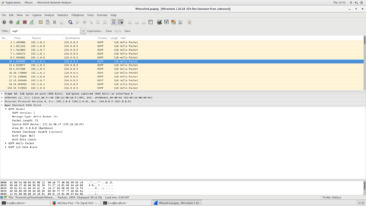
This is where things started to take unplanned turns. A lot of people read a little too deep into the question and started to run GeoIP lookups for the address (it is a public address after all) and looked for locations other ways. Unfortunately not as many went the way I had planned. If you change your BPF to ip.addr==192.1.0.4 you see every packet that went to or came from that router. The vast majority of them are SNMP packets. It looks like someone is doing a walk of a big chunck of SNMP OIDs. There’s a number of ways to do it, but eventually you get to packet 741 and find OID 1.3.6.1.2.1.1.6.0. A quick google search for what that is comes up with sysLocation which is an arbitrary value that the admin can set that specifies where the device is located. While the value in the packet breakdown shows the hex string, if you look at the byte contents, you can easily see the flag ACSC{UnderTheMoon}.