I was doing some research for my firewall project that I wrote about the other day and wanted to add some system monitoring. I figured that the server that I host signal-chief off of didn’t currently have any monitoring going so I would use that (cause why test in the lab when you can test in production?). The system I decided to use was Tripwire which is an opensource project that is part of the Epel Linux repo. I put this together with help from a couple of different tutorials that I found online and combined.
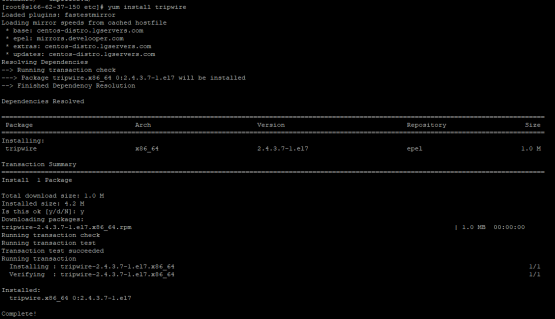
Instillation of Tripwire is pretty straight-forward if you already have the Epel repo added to your yum config. Just install tripwire
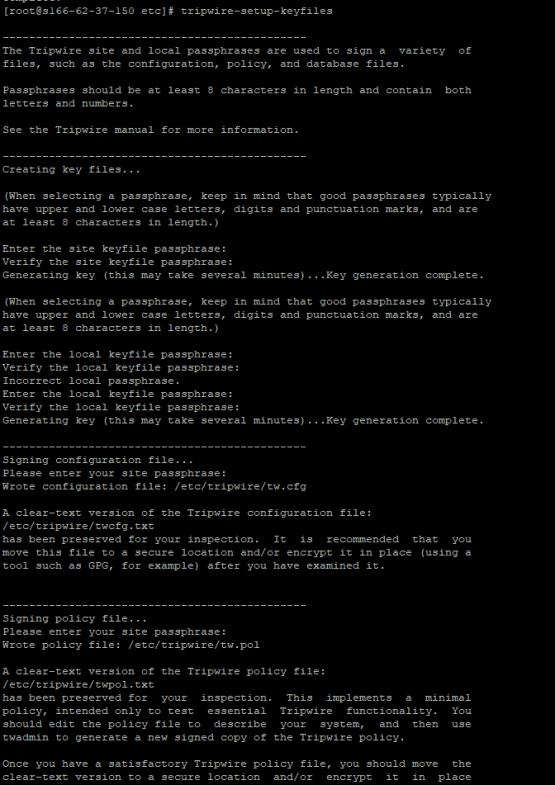
yum install tripwireThe next step is really to do the initial setup of Tripwire where it puts together its basic configuration files, and then signs the configuration files with a key. During this step, it asks you for a site and a local password. I honestly don’t know what the difference is so I just used the same password for both of them. I’m sure that’s probably not the most secure way to configure this, but for my purposes it works.
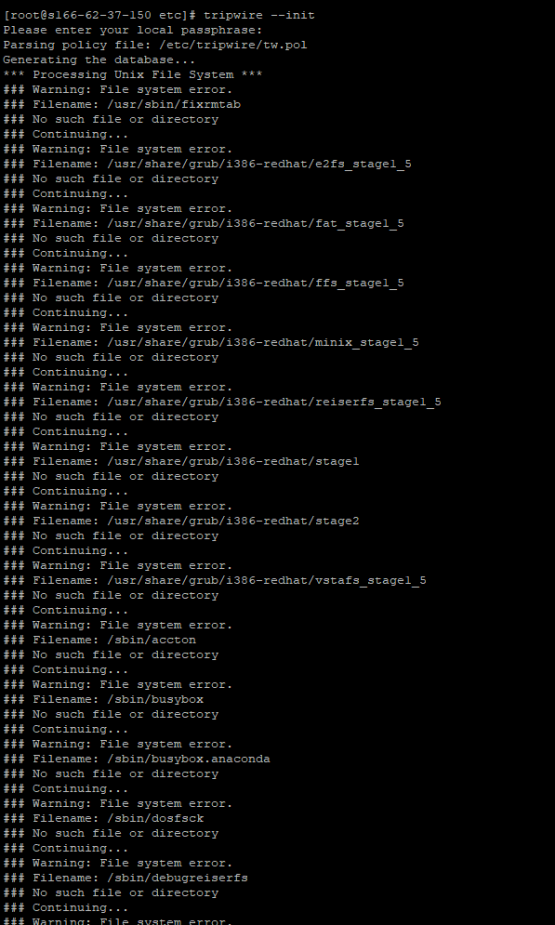
tripwire-setup-keyfilesNow that the basic files have been generated, we can initialize it with those basic configurations. This is done with the –init option. This first time we do this is going to generate a lot of errors for files that don’t necessarily exist on our operating system but are part of the default rule set. We’ll fix those errors in a minute.
tripwire --initNext, we’ll run an initial check of Tripwire. Again, we’ll get a bunch of errors but this time we’ll pipe a list of those missing files to a temporary file called no-dir.txt
tripwire --check | grep Filename > no-dir.txtNow using a little bit of sed magic, we’ll comment out all of the lines in the configuration file that reference files that don’t actually exist. This was done using the following command. This command goes through the file that we just generated and extracts the 2nd field (The file name itself). Then with sed it goes into /etc/tripwire/twpol.txt and finds all occurrences of that line and appends a # to the start of the line to comment it out.
for f in $(grep "Filename:" no-dir.txt | cut -f2 -d:); do
sed -i "s|\($f\) |#\\1|g" /etc/tripwire/twpol.txt
doneNext we’ll recompile the rules and the re-initialize the program. After that, we’ll run a check and make sure it comes back without any errors.
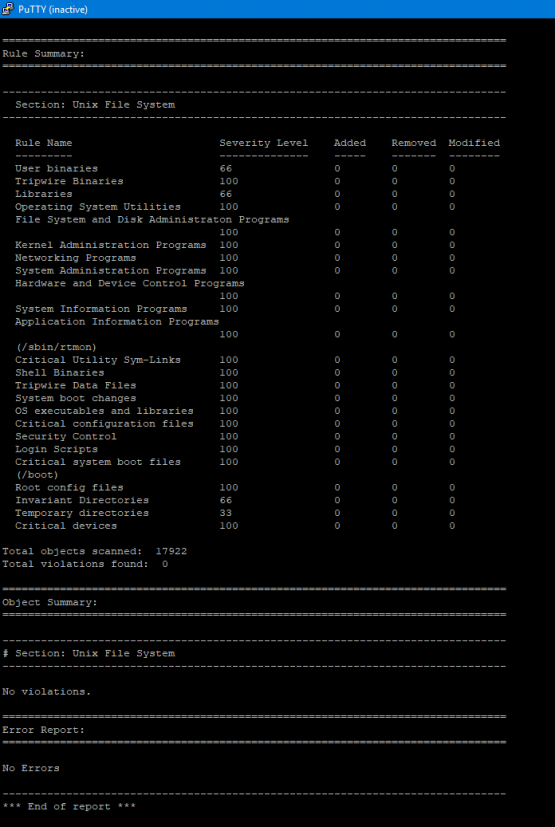
twadmin -m P /etc/tripwire/twpol.txt
tripwire --init
tripwire --checkOK, so it’s up and running now, but it only keeps the report local on the server. I for one don’t log onto the server unless I have to so it’s much better to just email it. Lets make sure that the server can send an email.
tripwire --test --email email@gmail.comIn theory, you should get an email with a test message in it. If you did, then great and if not, it probably doesn’t work. Now you have to configure the twpol.txt file with the email. Unfortunately I haven’t figured out an easy way to do this yet. You have to go in and an “emailto” line each section of the config (and there’s like 20 of them). See the example below.
# Ruleset for WordPress
(
rulename = "Wordpress Data",
severity= $(SIG_HI),
emailto = myemail@gmail.com
)
{
/var/www -> $(SEC_CRIT);
}Now time once again to recompile the config and then run a test.
twadmin -m P /etc/tripwire/twpol.txt
tripwire --init
tripwire --check --email-reportLast but certainly not least, time to automate this with a cron job so that the job will run daily. Add the following line to your cron.d config
0 0 * * * tripwire --check --email-report