Continuing on with some write-ups from the Hack the Box Cyber Apocalypse 2024 event. This one wasn’t particularly difficult, but it was a pain and time consuming. I went through this process manually but one of these days I’ll have to see if I can find a way to script it out and make it appear faster.
Overview
Type: Forensics
Difficulty: Medium
Description: In the shadowed realm where the Phreaks hold sway, A mole lurks within leading them astray. Sending keys to the Talents, so sly and so slick, A network packet capture must reveal the trick. Through data and bytes, the sleuth seeks the sign, Decrypting messages, crossing the line. The traitor unveiled, with nowhere to hide, Betrayal confirmed, they’d no longer abide.
Files: forensics_phreaky.zip
Process
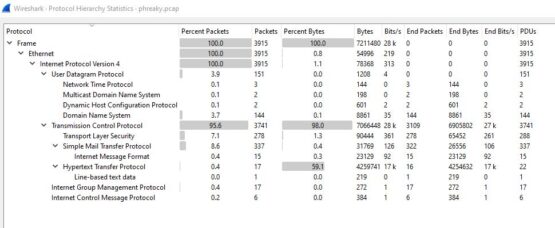
Within the zip file is a pcap file called pfreaky.pcap. I went ahead and opened up the file with Wireshark and went to work. When I used to teach, the first thing I would have my students do when they were looking at a pcap is to look at the protocol hierarchy (Statistics > Protocol Hierarchy). Its great because it give a single place to get a rough idea of what we’re looking at in the file. The challenge prompt sort of implies that there is exfil going on and looking at the statistics, I see a that nearly 9% of the included packets are SMTP (email) packets which as good a way to move data as any other. I went a head and applied “smtp” as a filter so I could see just those packets.
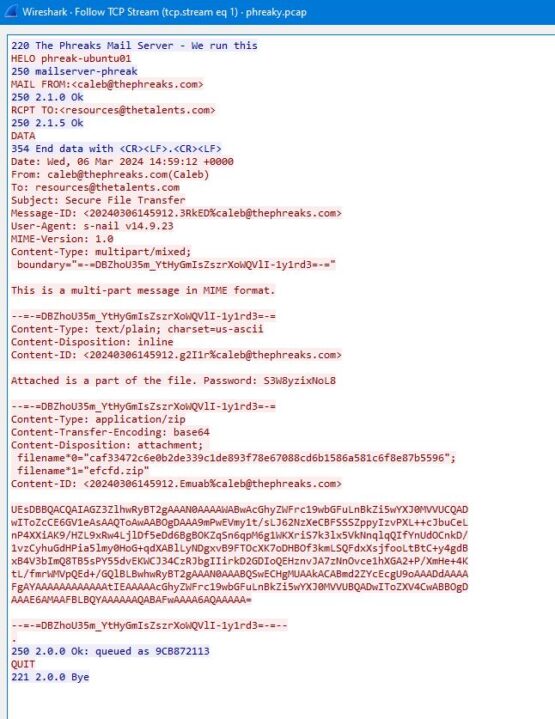
Right clicking on the first packet and selecting Follow > TCP Stream build a filter for that stream only and also combines it together into a full conversation. Looking at it, we see the full SMTP connection where “The Freaks Mail Server” is sending an outgoing message message. The message was sent on 3/6/24 at 14:59:12 Z from caleb@thefreaks.com to resources@thetalents.com with a subject “Secure File Transfer”. Ok, that definitely looks like exfil. Looking at the body of the message you see reference to a password and then an attached file (in this case named efcfd.zip.
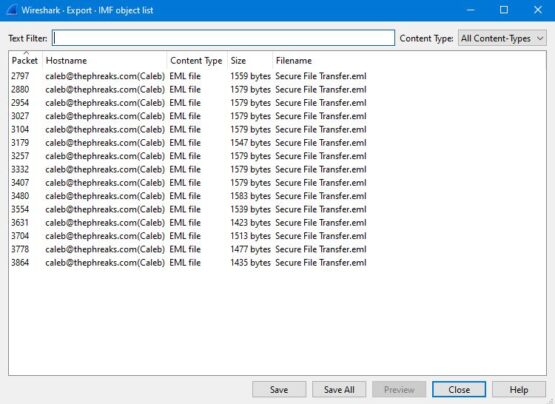
I will be the first to admit that the easy way to do this is to just do it in bulk by going to File > Export Objects > IMF which will save all of the Internet Message Files (IMF) as regular email messages which you can then open up on outlook or your email client of choice. That being said, doing so leaves you potentially exposed to badness (not really a problem with a CFT but real problem in real life) and also isn’t the most forensically sound idea either.
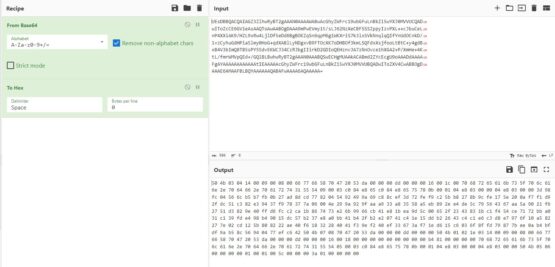
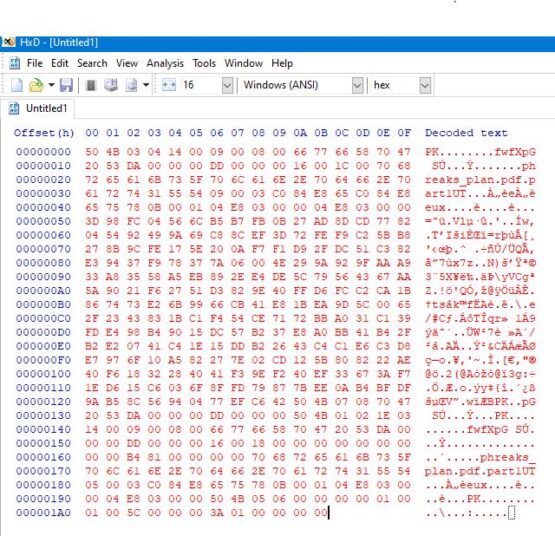
Opening up CyberChef again, I put the base64 encoded attachment into it and export it into hex. I open up HxD (my personal favorite hex editor) and create a new file, paste the hex contents into it, and save it as 1.zip (this just happened to be TCP conversation 1). Opening up the zip file and I see a file called “phreaks_plan.pdf.part1”. I extracted the file using the password contained in the email. Just based on the fact that the actual file extension is “.part1”, it implies that there are multiple parts.
Opening the file itself up with HXD and the start of it looks like a valid PDF file but the end of it is definitely not. I love Gary Kessler’s website which contains the magic bytes (first few bytes) as well as the end of file markers a huge number of files. Its a resource I used to use fequently when I was teaching. There are a few end of file (EOF) markers for PDFs, but the ASCII for them all include “%%EOF”. As you can see, the file we opened doesn’t. Combined with everything else, this must be a file fragment. I opened a new file in HxD and copy/pasted the contents of the fragment into it. I went ahead and repeated this process for each of the SMTP messages.
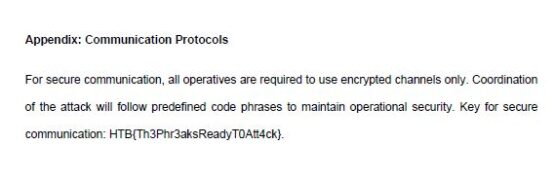
Once I’ve put all of the file fragments into a new file, I saved it as a pdf and opened it up. Down at the very bottom of the file is the flag.