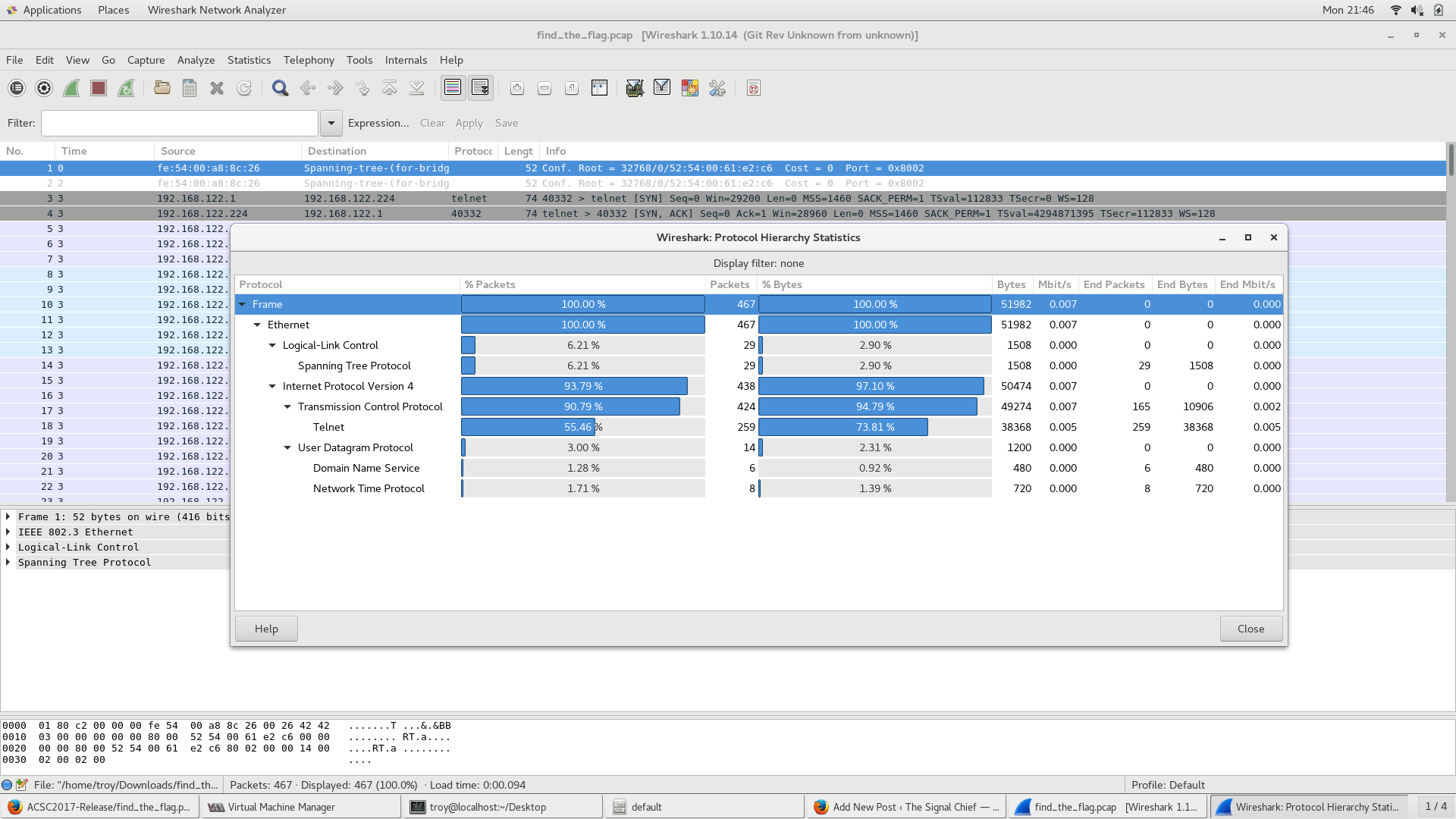
Another quick walk-through from ACSC5. This problem is called find_the_flag. Problem: Someone thought that using telnet was a good idea. Guess this should make your job a lot easier…..Find the flag
We’re Mobile Friendly
I’ve had a number of things on my todo list for a while. One of them has been to update Signal-Chief to make it mobile friendly because I’ve noticed that a fair number of people tend to check us out with their cell phones or tablets. At long last, I have finally done that. I just got done creating a new Wordpress theme based on the Foundations framework. This allowed me to make the site adaptive to various screen sizes very easily so you can read it regardless of what device you are using to check it out. Additionally, I also upgrade the server that I host off of to hopefully make it perform a little bit better. Take a look around and let me know what you think.
January (well February) Warrant Officer Selection Results
So after the first government shutdown delayed the meeting of the selection board last month, HRC today published the results for the January/February Warrant Officer selection board. This board looked at 255A and 255N.
Congress Blames the Wrong Guy
A couple of days ago, I posted an article about some some possibly non-public military locations being discovered after fitness tracker company Strava put up a heat map of their users activity. In the 48 hours or so that has passed 9 Democratic members of congress wrote a letter to Strava asking for information. The letter makes a number of statements and asks questions that I think look to shift the blame of all of this on Strava instead of the military and the individuals who were wearing fitness trackers and publicly broadcasting their location information. I will go through a number of points and include my own response.
Spilling the Beans
I am in Augusta for the next few weeks for the ARCYBER Work Role Working Group (WRWG) and some training. While I was waiting for my plane yesterday, I came across a story in my news feed talking about how publicly available GPS data may have exposed the location of classified US bases overseas
FY 18 Warrant Officer Promotion Board
Well just over a month after they finally released the results of the FY17 promotion board, it’s time to get ready for this years board. MILPER message 18-021 was released on the 18th
whats_my_password
Another quick walk-through from ACSC5. This problem is called whats_my_password.
Problem
What is that administrator’s password? Note: enter the flag in the format acsc2017{}
find_the_stack2
The is a follow-on to the first find_the_stack problem from ACSC5. This was originally supposed to be the third one in a series of challenges based on this problem but I had some problems with number two so this became number two.
find_the_stack
This is the first of what will hopefully be many walk-throughs from various CTF competitions I’ve competed/worked on. This first challenge is a simple one that I created for the 5th annual Army Cyber Skills Challenge.
Net Neutrality
Earlier this week, the FCC, “lead” by Ajit Pai voted to repeal its policy of Net Neutrality. The policy was put into place in Feb 2015 after the FCC (at the time under the Obama administration) made the decision to classify ISPs as a public utility under Title II of the Telecommunications Act. For a lot of people (myself included for a while), this doesn’t make a lot of sense what any of this means so let me try to take a few minutes to explain (at least my understanding of it).