Last week was the 6th annual Army Cyber Skills Challenge (ACSC) hosted by my home unit, 780th MI Brigade. If you don’t recall, I first wrote about ACSC about this time last year. This was the 2nd year in a row that I served as the OIC for the event, and it was truly bigger »
Chicken or the Egg
I was browsing through the 255N Facebook group when someone posted this comment that got a good discussion going. There were several great points that were brought up in the conversation and I posted a short answer myself but I thought that the topic deserved a little bit more discussion.
Sept Board Results
I want to take a minute and welcome the newest members of the Warrant Officer Corps.
Warrant Officer Promotions
For the first time in a very long time, the warrant officer promotion board results were actually released in the same FY as when the board actually met! First let me say congrats to everyone that was selected for promotion. Before I go into the numbers, let me preface this by saying that these numbers »
Computer Network Operations Development Program
Late last week HRC released MILPER message 18-264 which announced applications for the Computer Network Operations Development Program (CNODP). For those of you not familiar with it, CNODP is the Army’s school for training future cyber tool developers.
Honey Pots Get a Little Less Sticky
The other day a friend of mine shared a link to a new academic paper that was just released by a couple of researchers at the University of Cambridge. The team, Alexander Vetterl and Richard Clayton, wanted to see if they could create a technique to identify publicly accessible honeypots without having to actually interact with them.
COMSEC Is Dead….Long Live COMSEC
Whenever the Army creates a new Military Occupational Specialty (MOS), they have to fill it with bodies initially that aren’t actually the MOS. In late 2013 the Army graduated its first class of the new 25D Cyber Network Defender MOS. Shorty there after, the 25D, were placed into the unit COMSEC vaults to do a job that they were never designed to do.
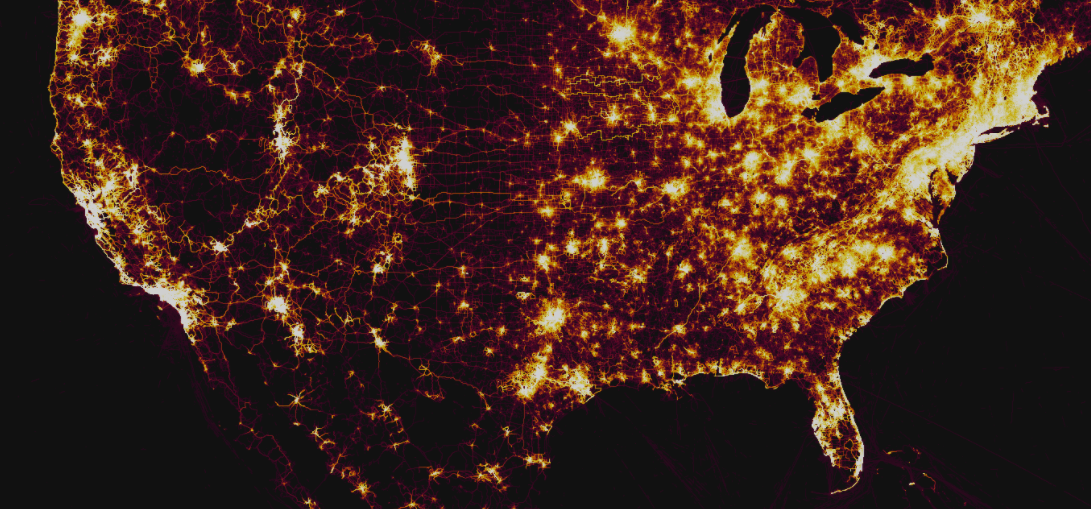
DOD Bans Wearable GPS
A few months ago, I wrote a story about the uproar that occurred after it was Strava released a heat map that showed it’s users working out and in the process revealed the location of classified military installations. Today the DOD announced that it had updated it’s policy for the use of personal and military owned wearable GPS devices.
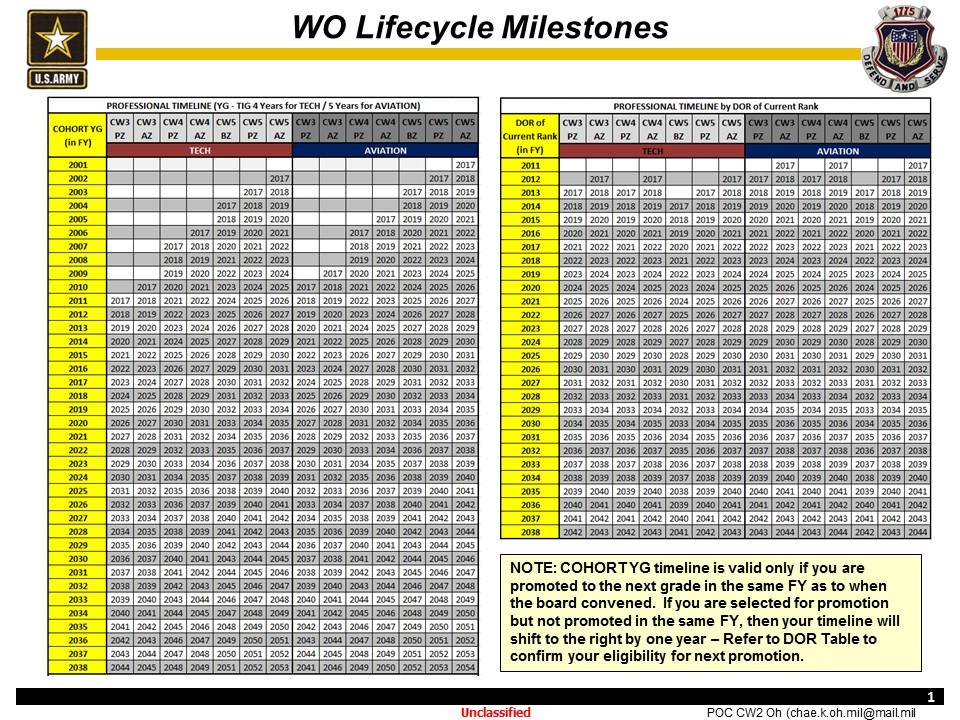
Promotion Timeline
I was browsing the 255N Facebook group earlier and saw that someone had pasted this handy graphic that shows when you promotion boards (assuming they don’t change anything) will meet. I figured it would be a nice little resource to add to everyone’s kit bag so here you go.
Cyber Chief
Yes that’s right after over 19 years of wearing signal orange I have traded it in for cyber grey.