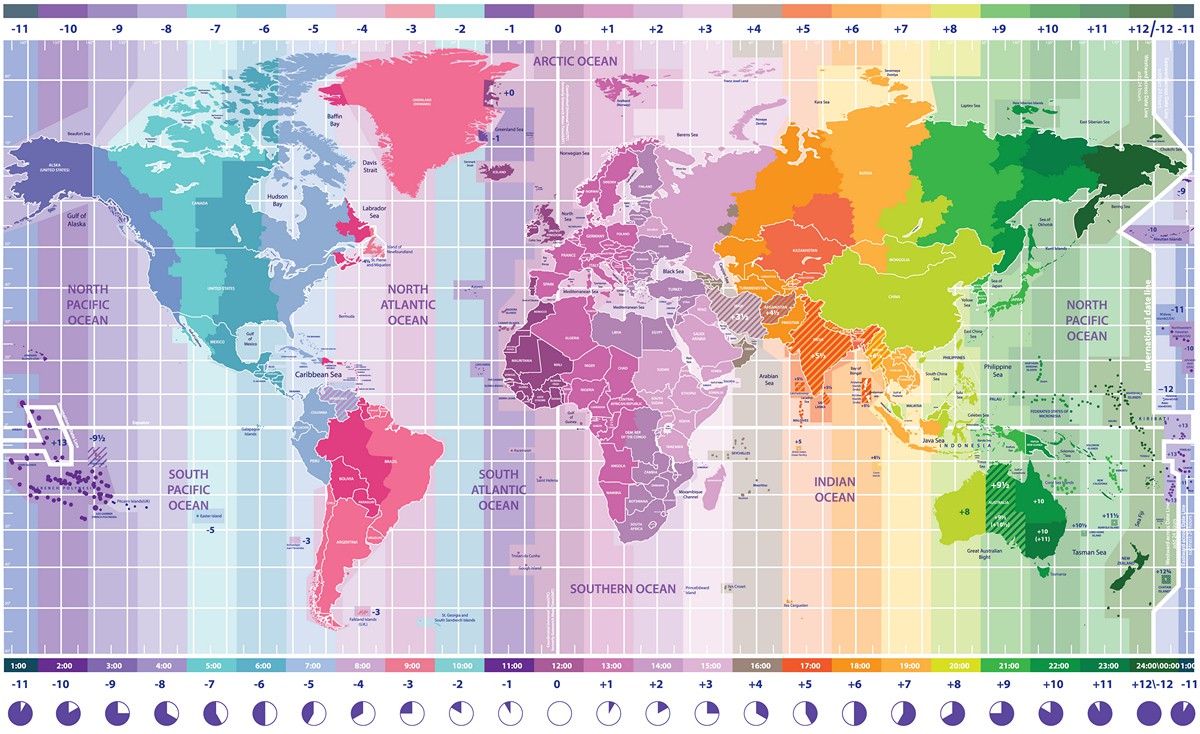
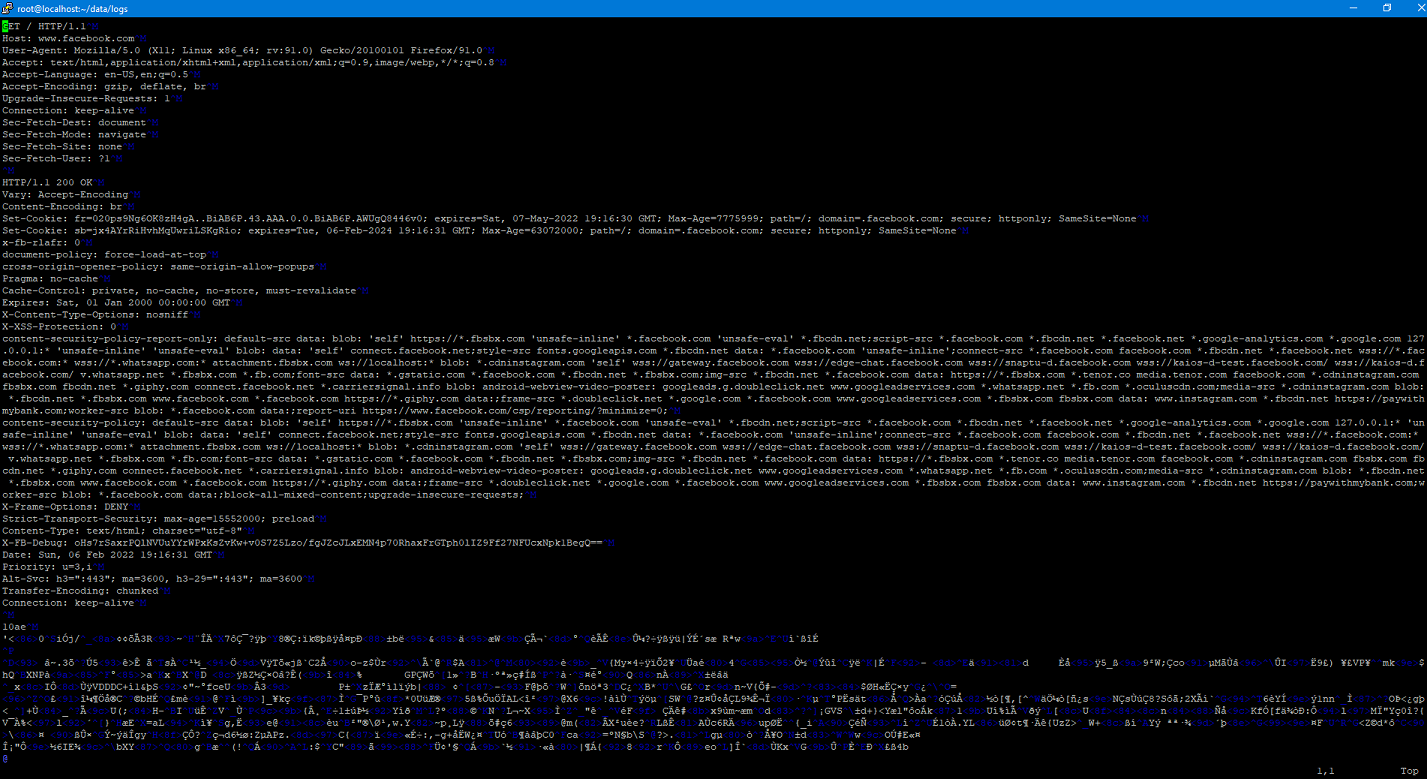
I am off for the next two weeks (more or less) so my goal is to check off a bunch of crap on my todo list that has been sitting on there for a while. One of those things that I’ve wanted to do was connect my server on AWS that is hosting Signal-Chief to »
Cyber Apocalypse – Phreaky
Continuing on with some write-ups from the Hack the Box Cyber Apocalypse 2024 event. This one wasn’t particularly difficult, but it was a pain and time consuming. I went through this process manually but one of these days I’ll have to see if I can find a way to script it out and make it appear faster.
Cyber Apocalypse – Urgent
Last weekend I jumped in and joined some co-workers for a capture the flag challenge hosted by Hack The Box. This is a walk-through (spoiler alert) for the forensics challenge “Urgent”
One More Time About Time
I’ve written about the importance of having accurate time before, and have always said that it can be difficult to keep a proper clock. I’ve always looked at it from a technical standpoint but a couple of days ago, one of my students sent me a video
and it caused me to look at the topic of time from a completely different perspective.
New Adventures
Today I am excited to announce that I have a new job! After spending the last year and a half or so at SEE, I’ve decided to make the move to SealingTech. While I love the team at SEE, SealingTech offered me a new adventure.
Implementing SSLSplit
A couple of weeks ago I talked about using SSLSplit to at as a proxy so that I could examine the mechanics of a Docker pull. I decided to go ahead a set up a purpose-built VM just for this so I could easily do this again in the future. I wanted to go ahead and document (and share) the steps that I went through for this.
Mechanics of Docker Pull
Recently I’ve been in the process of building an offline repository of software for a project at work. The idea is that we’ll be able to completely install all required software completely disconnected from the Internet. When it got time to deal with containers…challenges abounded.
Unique Identifiers of a Fresh Kali Image
The act of attributing a cyber attack is a long sought after, but rarely attained goal. While things such as techniques, IP addresses, and other artifacts can plan an important role in attributing an attack, being able to attribute actions to a specific computer that has been obtained can help provide overwhelming proof of an act. In this post, I’m publishing a paper that I started working on a few months ago (life gets busy) that provides a forensic analysis of multiple freshly installed Kali systems. My goal over the coming months is to conduct similar experiments on other operating systems. I’ve also provided the raw data that I used to conduct my analysis.
Advent of Code Day 9
For day 9, we’re trying to break a simple encryption scheme. Our input starts with a preamble of 25 numbers. From there, it continues with a series of additional numbers. Each number must be equal to the sum of any two of the previous 25 numbers. We’re trying to find the first number that doesn’t meet that rule.
Advent of Code Day 7
Day 7 threw me for a loop. Basically what you have is a remake of the Matryoshka Dolls where you have a doll inside of a doll, only in this case it was bags within bags. We’re provided with a list of rules telling us which bags are within which bag. Ultimately we want to find how many bags can contain a “Shiny Gold Bag” within it.