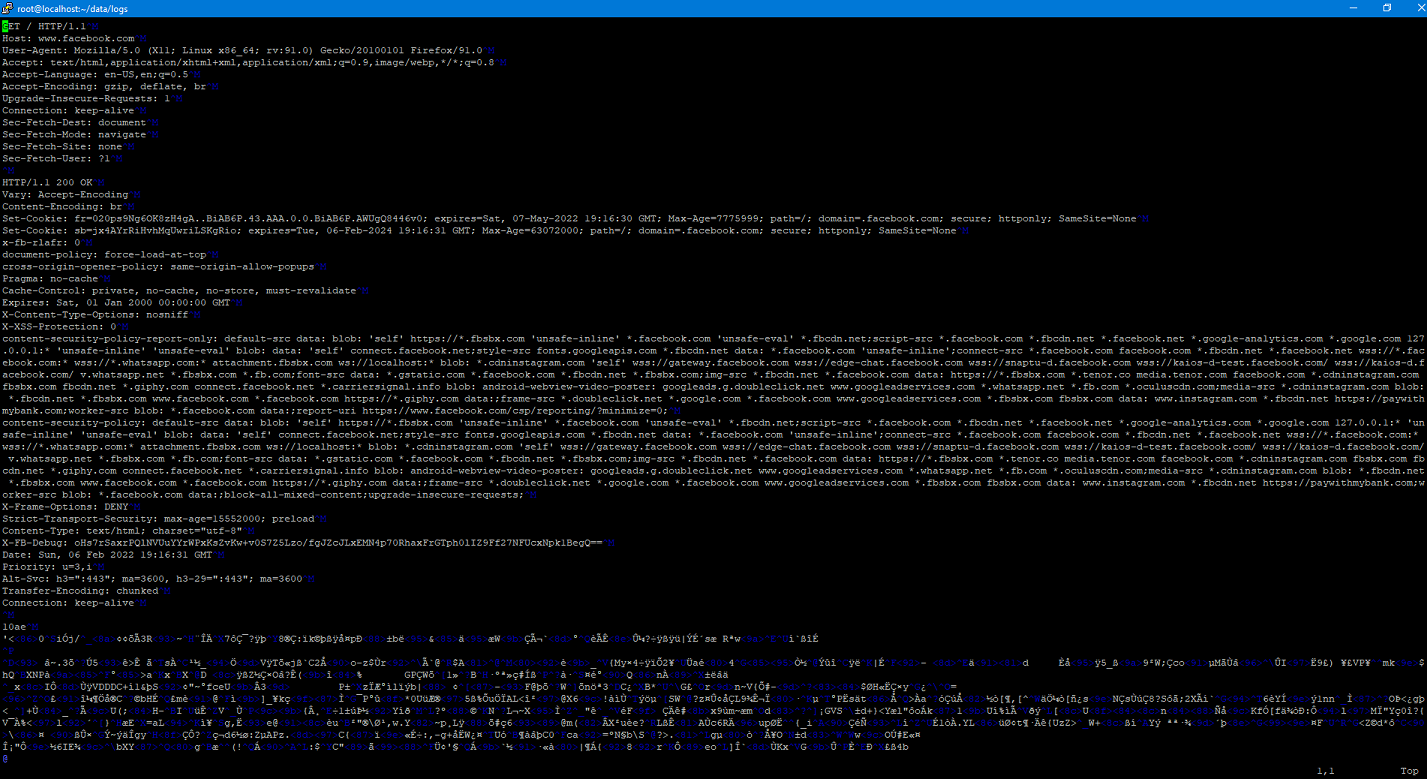
A couple of weeks ago I talked about using SSLSplit to at as a proxy so that I could examine the mechanics of a Docker pull. I decided to go ahead a set up a purpose-built VM just for this so I could easily do this again in the future. I wanted to go ahead and document (and share) the steps that I went through for this.
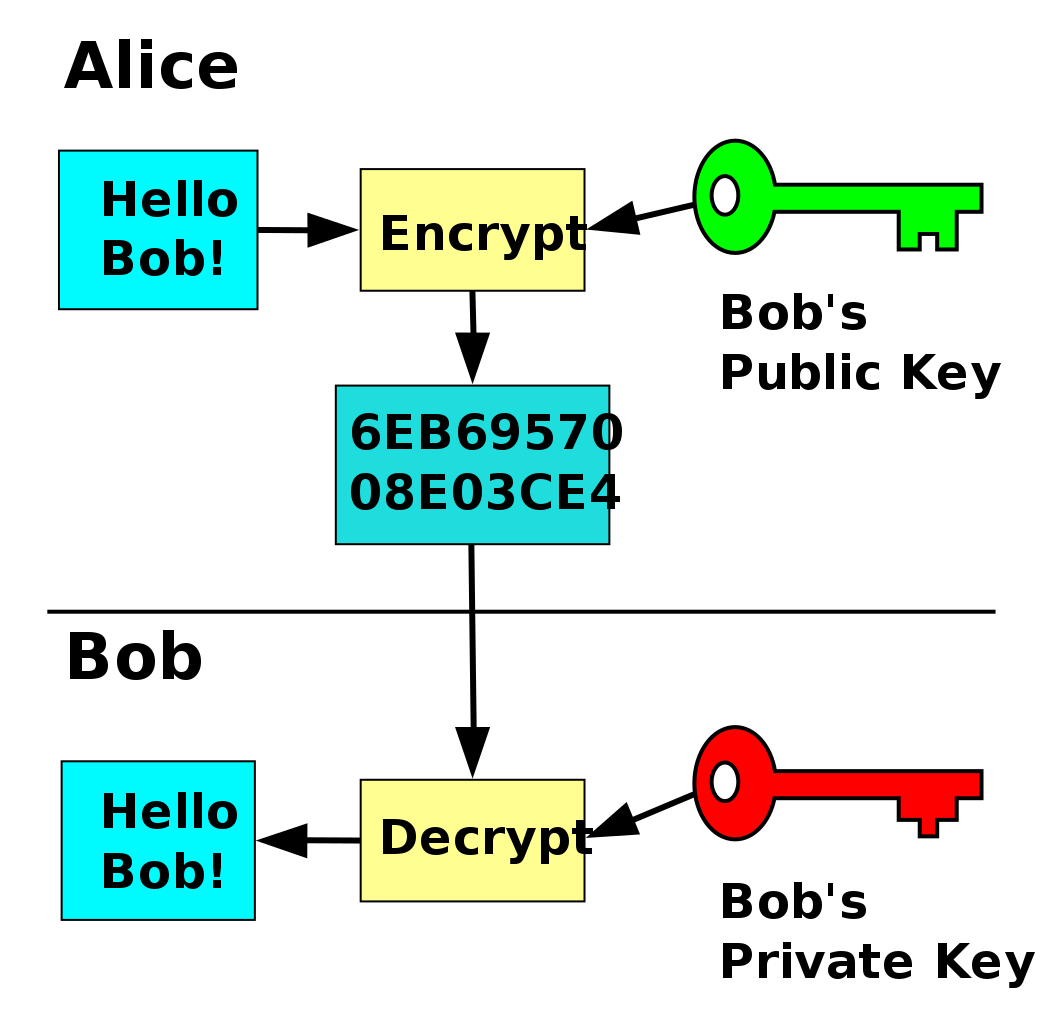
Asymmetric Encryption for Dummies
I’ve always found encryption interesting. While I’m not a mathematician I understand the basics generally. That statement mostly holds true when it comes to a symmetric encryption, but not so much when we start talking about asymmetric encryption.
Defensible Security Architecture Certified
On Friday, I sat for the GIAC Defensible Security Architecture (GDSA) exam. The certification is brand new and is based on the SANS Sec 530 course. While I passed, it didn’t go the way I had planned
DNS Over HTTPS
You may have noticed recently that Comcast and a number of ISPs have started to fight with Google and Mozilla after the makers of Chrome and Firefox announced that they were going to start support the use of DNS over HTTPS (DOH) and DNS Over TLS (DOT) recently
Identity Awareness, According to the DOD
Brought to you by the same group that thought that thought that Jeff and Tina were the way to get us to be cyber aware has now released their “Identity Awareness, Protection, and Management Guide”.
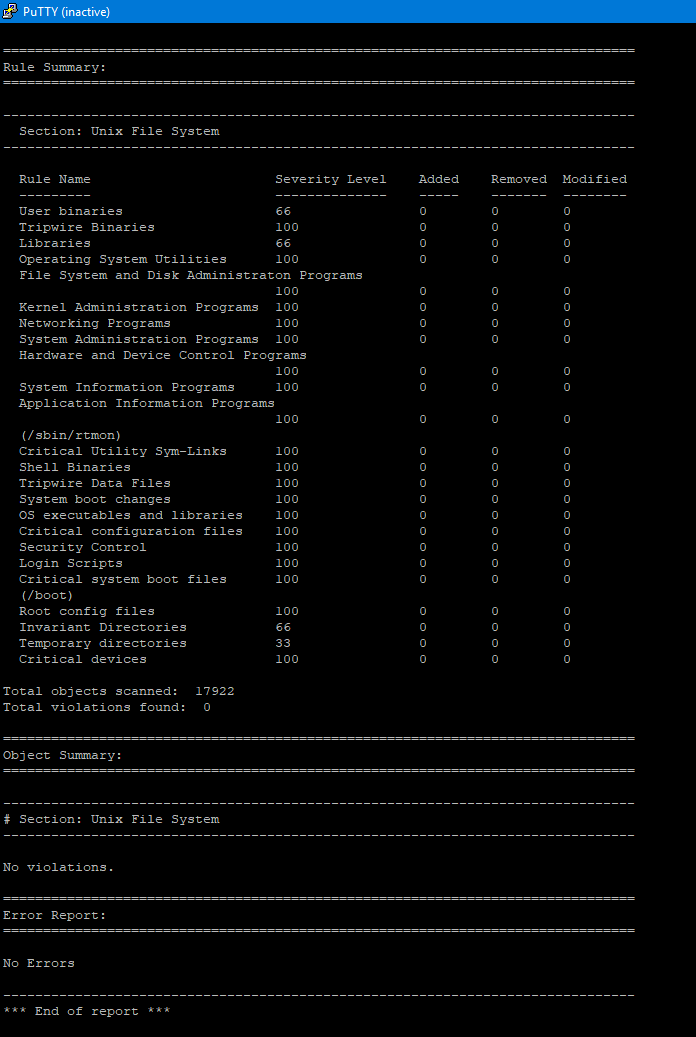
Setting up Tripwire
I was doing some research for my firewall project that I wrote about the other day and wanted to add some system monitoring. I figured that the server that I host signal-chief off of didn’t currently have any monitoring going so I would use that (cause why test in the lab when you can test in production?). The system I decided to use was Tripwire which is an opensource project that is part of the Epel Linux repo. I put this together with help from a couple of different tutorials that I found online and combined.
Birth of Spam
So this morning I was listening to the radio on the drive into work when the DJ made an interesting statement. Turns out….he was right. Today marks the 40th anniversary of the very first spam message.
Mandiant 2018 Trends Report
For anyone who doesn’t know, Mandiant is large cyber security company that was bought by Fireeye. They grabbed a lot of attention by the cyber security community when in 2013, they publicly released a report that linked the Chinese military to attacks dating back to at least 2006 on over 141 organizations. Each year they release a report on cyber security trends that they observed during the previous year. Granted, the results are screwed because they are based only on incidents that they responded to, but they at least give a good overall picture of what is going on around the world.
Congress Blames the Wrong Guy
A couple of days ago, I posted an article about some some possibly non-public military locations being discovered after fitness tracker company Strava put up a heat map of their users activity. In the 48 hours or so that has passed 9 Democratic members of congress wrote a letter to Strava asking for information. The letter makes a number of statements and asks questions that I think look to shift the blame of all of this on Strava instead of the military and the individuals who were wearing fitness trackers and publicly broadcasting their location information. I will go through a number of points and include my own response.
Net Neutrality
Earlier this week, the FCC, “lead” by Ajit Pai voted to repeal its policy of Net Neutrality. The policy was put into place in Feb 2015 after the FCC (at the time under the Obama administration) made the decision to classify ISPs as a public utility under Title II of the Telecommunications Act. For a lot of people (myself included for a while), this doesn’t make a lot of sense what any of this means so let me try to take a few minutes to explain (at least my understanding of it).