HRC has posted MILPER Message 15-258 seeking applicants for the Computer Network Operations Development Program (CNODP) class of 2019. This is a highly advanced program whose graduates are the developers of the Army’s future CNO tools.
ATP 6-02.75 (Techniques for COMSEC Operations) has been released
The Cyber Center of Excellence has released ATP 6-02.75 (Techniques for COMSEC Operations). It’s stated purpose is to: Provides guidance on the management, employment, handling, and storage of communications security materials.
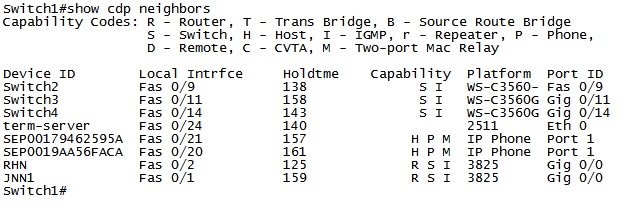
Cisco Discovery Protocol (CDP)
When there is a problem with the network, time matters. We need to be able to quickly move from device to device in order to identify and rectify the problem. In order for this to occur, we have to know where to go to next, and how to get there.
Cyber is Here
For anyone who doesn’t regularly check the MILPER message site you may have missed three separate messages that were released last week that directly affect signal warrants and our Soldiers. As you probably know, the Army is in the process of manning its new Cyber Branch. The officers got their chance to cross over earlier this year and it looks like the same is finally true for the warrants and Soldiers.
What Time Is It?
Let me give you a scenario. You are having some problems on the network that are spread across several devices. You go into the log file of each device and see a bunch of messages with a mix-match of various times that mean absolutely nothing to you. In short, you have no idea what is going on with your network.
Protecting Printers
The Army, and the world in general, has been slow to accept the fact that anything on a network can present a risk to that network. Routinely, we’ll place a device on the network without properly configuring it, patching it, or securing it without a second thought. Even on the occasion that we do think about the security of that device, we look at the device as being unimportant and it doesn’t really matter if it is compromised. Today we’ll talk about the threat sitting in the corner of the TOC….the printer
Have you seen my image disk?
Imagine this. Your brigade is part of a Corps level task force preparing to move into an allied country to push out an invading Army. The unit has been on site for several weeks and is just waiting for the order to attack. One day you get a call from one of your battalions informing you that their SIPR call manager has crashed and that they will need to reimage the system. You reach into your box of CD/DVDs to find the call manager disks and discover that you don’t have it…..FML
How to Steal a Password in 15 Seconds
People often wonder how hackers are able to get people’s passwords in order to access their accounts. Truth of the matter is, it’s really not that freaking hard. Check out the video below from Jimmy Kimmel and pay attention to two things. 1. Just how weak their passwords are and 2. Just how easily the interviewer got them to give up the passwords.
Care to save America from Evil (at least in cyber space)?
This is for all of the NCOs that read this (and all of you Warrants who have NCOs that are computer nerds like many of us). As you have probably heard, the Cyber Center of Excellence, (aka…Fort Gordon) is looking for senior SGTs and above who are interested in becoming the founding group of 25Ds (Cyber Network Defender)
Trends from the National Training Center Part 6 – Network Security
Our networks play a vital part in allowing the units we support to communicate which enables to commander to “impose his will on the enemy” (a my boss likes to always say). But if the network is not secure it can easily be used against us. This is part six of a series of posts concerning the network trends that I regularly see here at the National Training Center as units pass through on rotation.