By and large I personally think that most of us are much more comfortable with layer three than any other layer in the OSI model. We deal with it each and every day. We have a number of tools at our disposal which make it very easy for us to see if/when it’s working and just how the data is traveling. To start with though, we have to know just how things are supposed to work.
Getting from A to Z
When I entered the Army in July 1999, I came in as 31F (switch operator). Anyone who worked with MSE will remember that it had almost absolutely no data capabilities, but also that it was extremely easy to troubleshoot. Signal flow for MSE was pretty darn easy to understand. If you understood the idea of how the system worked, the signal flow was easy to follow. With the introduction of JNN and IP data networks to tactical communications, logical and physical said “It’s been fun” and headed their separate ways leaving our operators and even ourselves busy scratching our heads wondering how the hell it all worked.
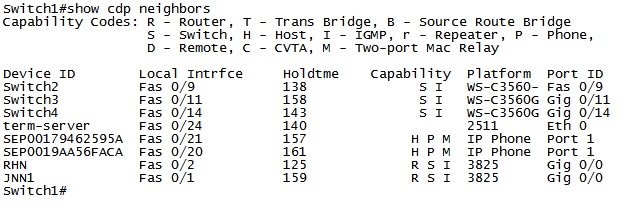
Cisco Discovery Protocol (CDP)
When there is a problem with the network, time matters. We need to be able to quickly move from device to device in order to identify and rectify the problem. In order for this to occur, we have to know where to go to next, and how to get there.
5 Router Commands That Saved My Life
We have all learned an important lesson in life the hard way. When it comes to working on the router or switch, there is often a couple of commands that you discovered after beating your head against the wall for a while that if you had known about them earlier, would have made your life so much easier. These are those commands for me.
But they didn’t teach me that in WOBC! – Comments in configs
There are a few things that are in WIN-T that are not explained in school. You either find yourself figuring it out or being told by another Warrant. How many of you have noticed that there are configurations available for all your equipment in TXT format? How many of you use them to blow in configurations when replacing gear from your spares? How many of you have read all the comments?
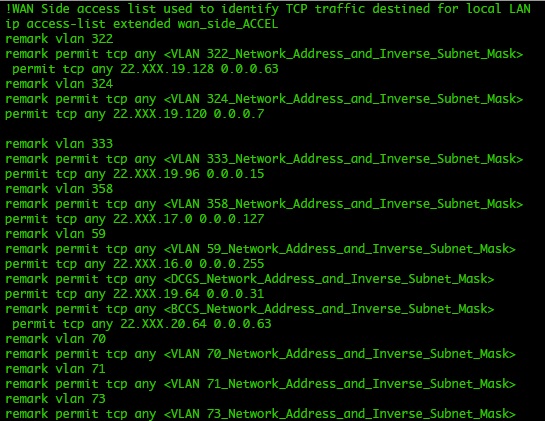
Which Way Do I Go SIPR Edition (Changing Routing)
A couple of weeks ago we talked about what affect changes to our network can have when we add HCLOS and other links between nodes. In that article, we talked exclusively about NIPR traffic going across the network and didn’t mention anything about SIPR. So what happens with our SIPR traffic if we install a HCLOS link?
What the hell Happened to the TACLANE?
A quick story for everyone today. A year or two ago a unit was coming through here on rotation. One of their CPNs was setup very close to the Brigade Main so the Net Tech made the decision to give himself some redundancy in his network and ran a piece of fiber between the two nodes. Life was good until one day he had to stow his dishes and all of a sudden, SIPR stopped working. Why?
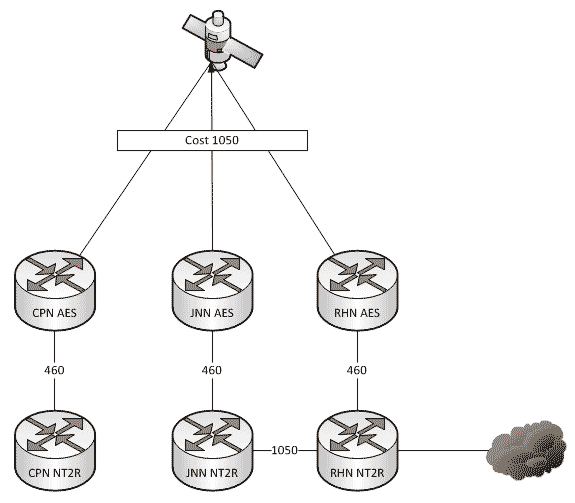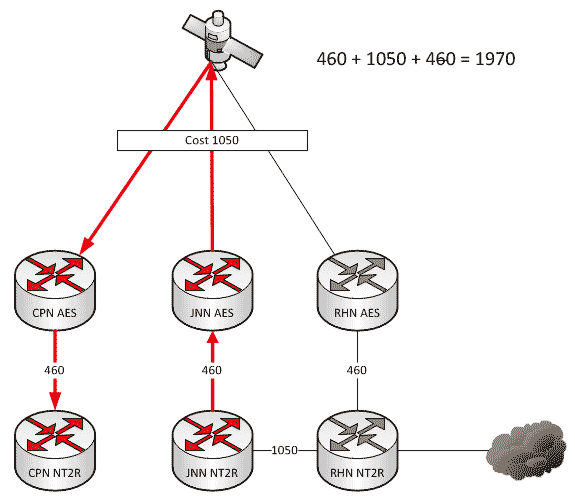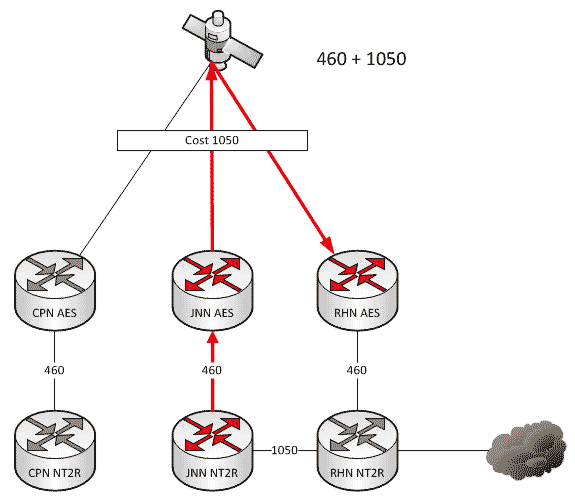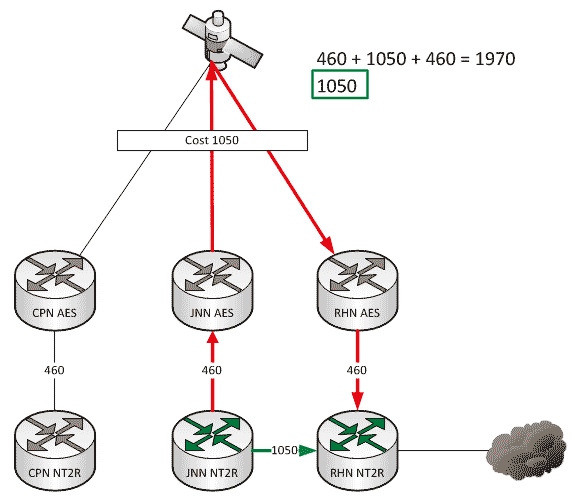
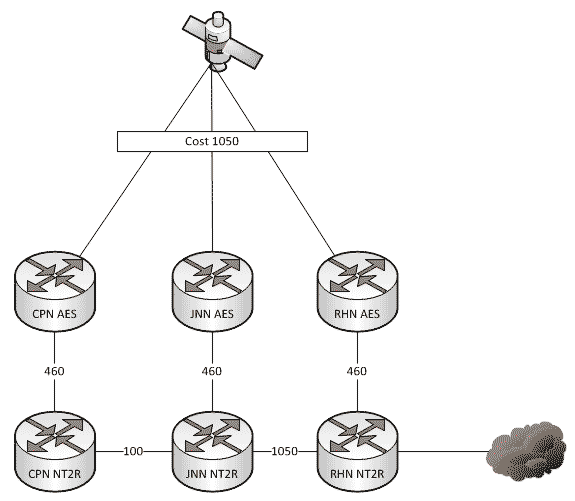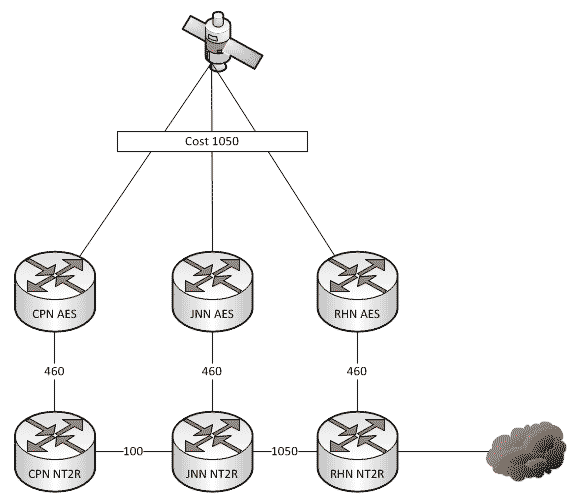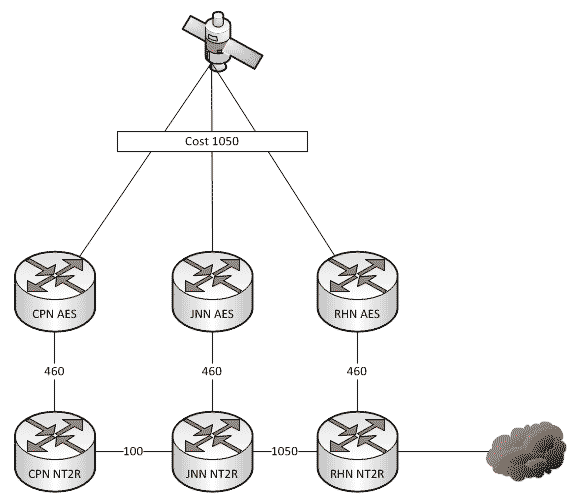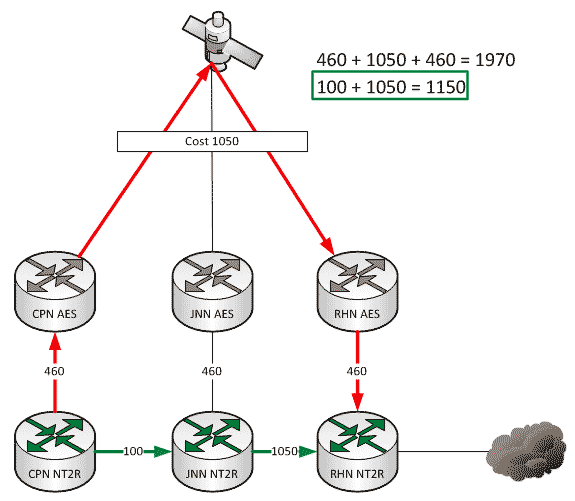
Which Way Do I Go? (Effects on Routing When the Network Changes)
As a general rule, all WIN-T nodes route traffic in pretty much the same way using pretty much the same configuration. We all know that at a CPN, both SIPR and NIPR traffic goes out the nodes TDMA link because, well, it has no other way to go. For a JNN, if the traffic is going to one of our subordinate units it goes out our TDMA, and if it is going somewhere else, it likely goes out our FDMA. We understand what it does, but most people have stopped thinking about why it does that. This is fine and dandy until we start making changes to the network.
Quality of Service (QOS) in WIN-T 1A
Quality of service (QOS) is one of those things that nearly every net tech has heard of but most know nothing about. We think of it as a silver bullet but are sorely mistaken. Take some time to learn about it and figure out how it can help you.
How to build your lab when you’re broke
As a network technician it is important to be able to continually practice your job, learn new things, and work to optimize the network when it’s in use. In a perfect world we would have a fully functioning lab environment where we can duplicate the tactical network, experiment, and roll out configuration changes in a controlled environment to see what effect they will have on the real thing. Unfortunately, that is not the case.