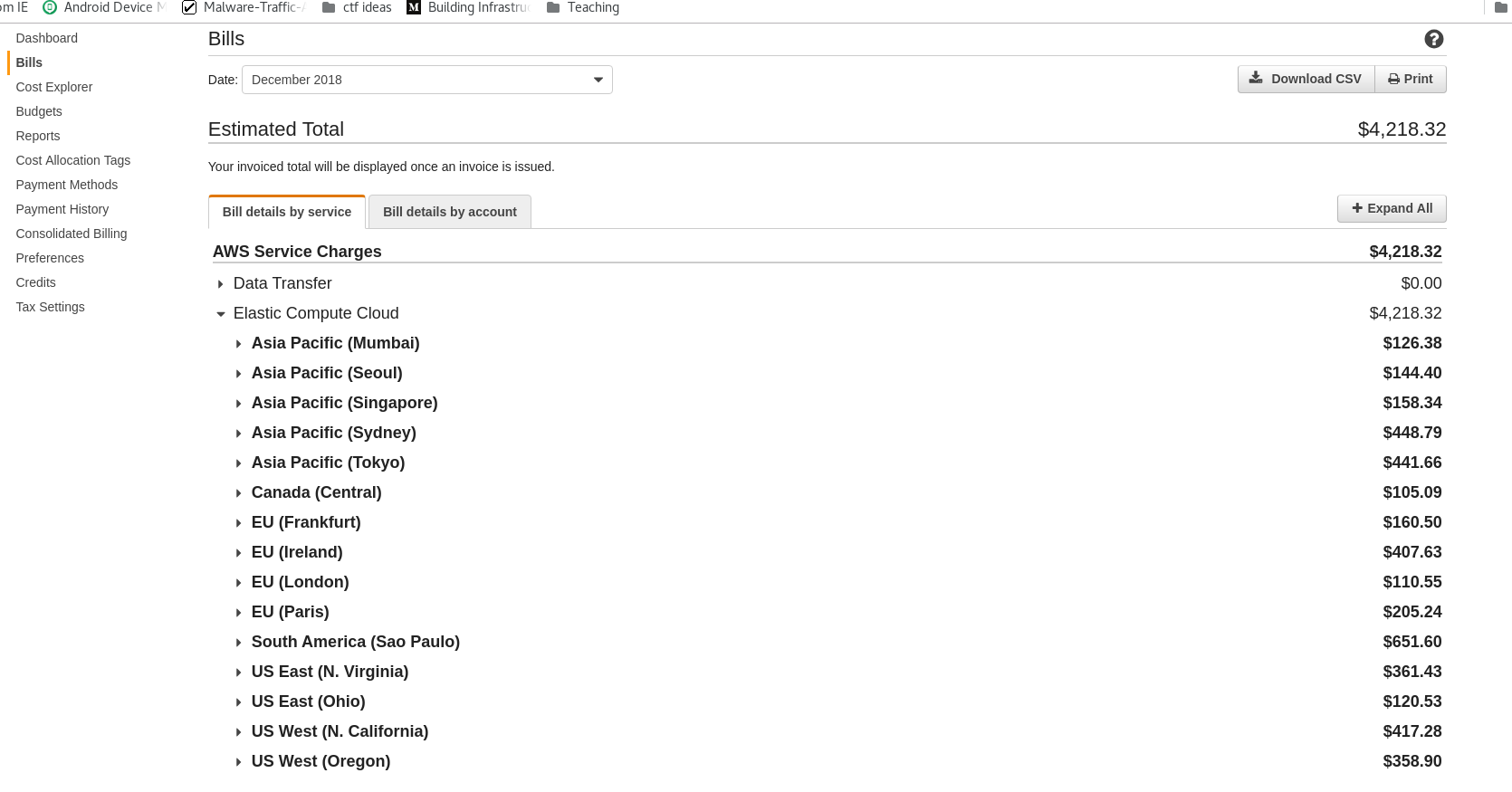
So I learned a pretty tough lesson today. I was doing some research for a project at work (which was going to be the original topic of today’s post) on which required me to setup a SOCKs proxy through AWS. I logged onto AWS, configured a small instance and went to spin it up when I got an error message saying that I didn’t have permissions to do this.
where_am_i
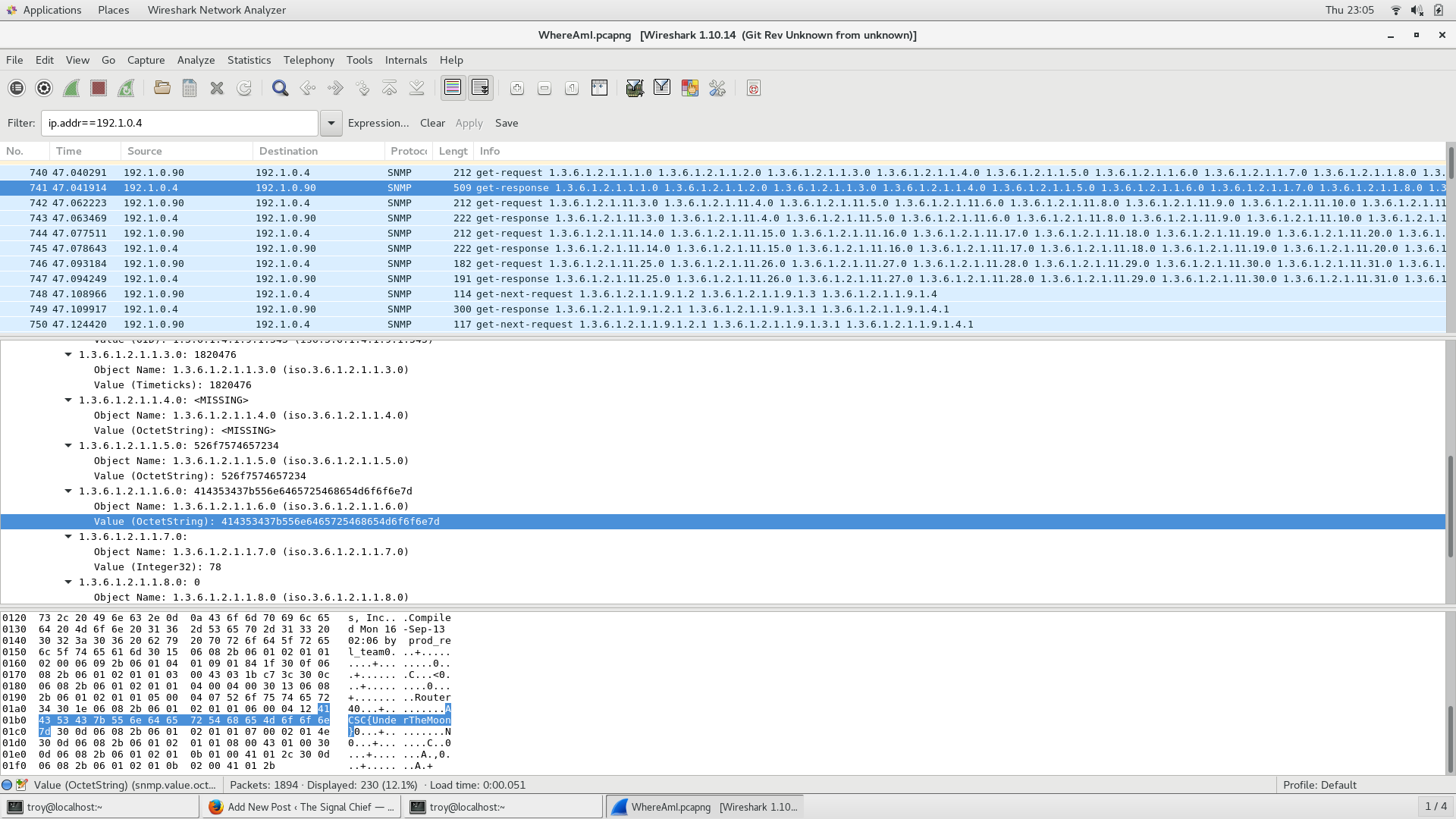
Another problem from ACSC5. You’ve been able to get on a router and capture some traffic in an effort to map out the the corporate network. Your intelligence team has told you that your target device has an IP address of 172.16.58.47 but no one knows that actual location of it. Examine the network traffic and see if you can figure out the location of that device.
Screwing Around with IPTables When It Doesn’t Play Nice
So you may not have noticed (hopefully) but I recently moved signal-chief from a shared hosting instance on GoDaddy to a dedicated VPS system. As a cyber guy, one of the first things I wanted to do was to start with some basic security so of course step one is to run yum update to update all of my packages, and step two was to setup some firewall rules. To allow me to initial a connection (DNS, http, whatever) from the server and get the return traffic back. Unfortunately when I tried to run this command I got “iptables: No chain/target/match by that name” sent back to me. Well that’s frustrating.