Continuing on with some write-ups from the Hack the Box Cyber Apocalypse 2024 event. This one wasn’t particularly difficult, but it was a pain and time consuming. I went through this process manually but one of these days I’ll have to see if I can find a way to script it out and make it appear faster.
Cyber Apocalypse – Urgent
Last weekend I jumped in and joined some co-workers for a capture the flag challenge hosted by Hack The Box. This is a walk-through (spoiler alert) for the forensics challenge “Urgent”
Implementing SSLSplit
A couple of weeks ago I talked about using SSLSplit to at as a proxy so that I could examine the mechanics of a Docker pull. I decided to go ahead a set up a purpose-built VM just for this so I could easily do this again in the future. I wanted to go ahead and document (and share) the steps that I went through for this.
Mechanics of Docker Pull
Recently I’ve been in the process of building an offline repository of software for a project at work. The idea is that we’ll be able to completely install all required software completely disconnected from the Internet. When it got time to deal with containers…challenges abounded.
Unique Identifiers of a Fresh Kali Image
The act of attributing a cyber attack is a long sought after, but rarely attained goal. While things such as techniques, IP addresses, and other artifacts can plan an important role in attributing an attack, being able to attribute actions to a specific computer that has been obtained can help provide overwhelming proof of an act. In this post, I’m publishing a paper that I started working on a few months ago (life gets busy) that provides a forensic analysis of multiple freshly installed Kali systems. My goal over the coming months is to conduct similar experiments on other operating systems. I’ve also provided the raw data that I used to conduct my analysis.
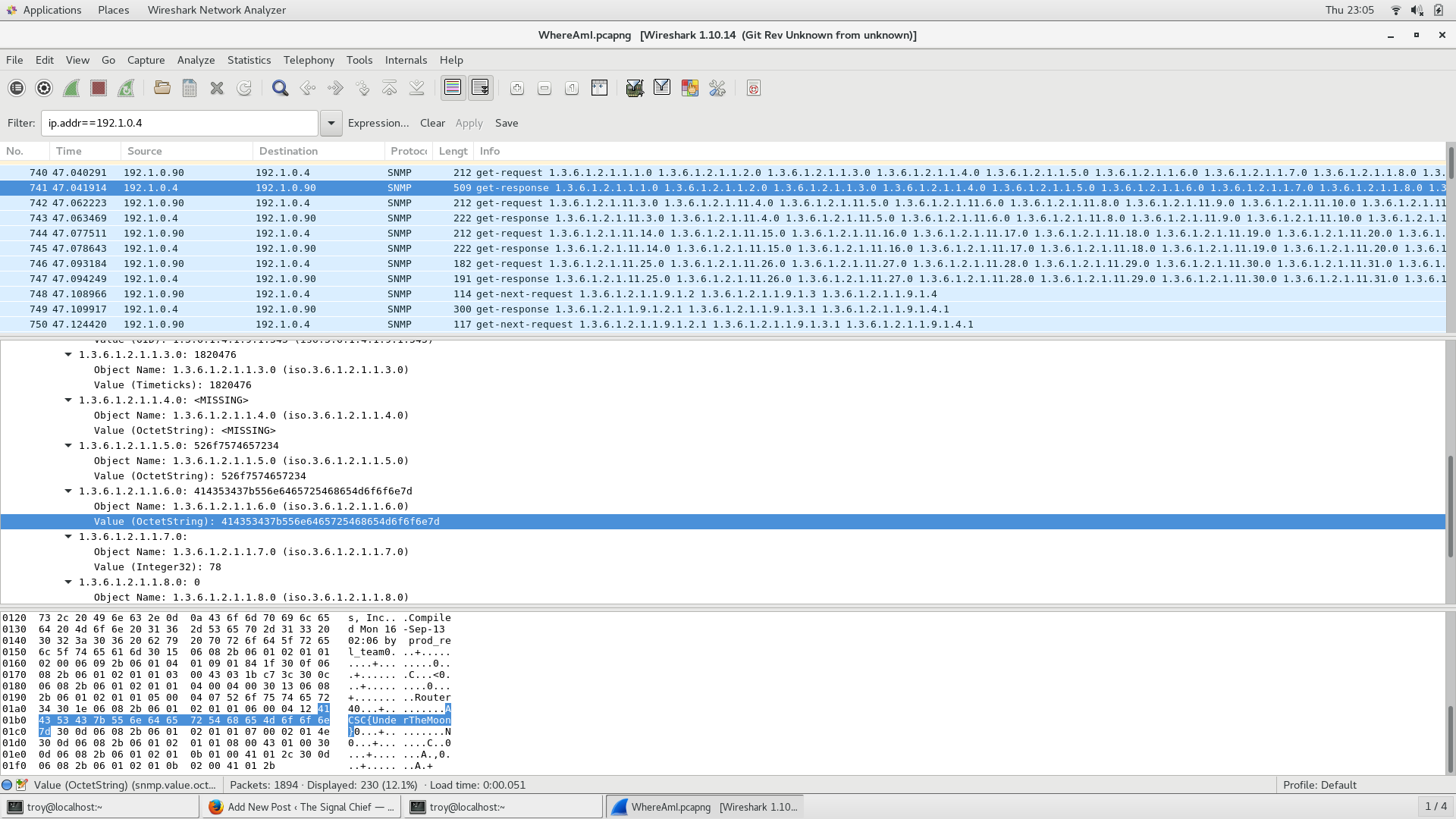
where_am_i
Another problem from ACSC5. You’ve been able to get on a router and capture some traffic in an effort to map out the the corporate network. Your intelligence team has told you that your target device has an IP address of 172.16.58.47 but no one knows that actual location of it. Examine the network traffic and see if you can figure out the location of that device.
animate_me
Yet another problem from ACSC5. Really not much of a clue needed, find the flag
Slow Mover
Another problem from the 5th annual Army Cyber Skills Challenge. The problem is called slow_mover and can be found here.
Problem
Your boss just handed you this PCAP that one of your network sensors captured. He’s positive that there is something fishy going on here but has no clue what it is.
find_the_stack2
The is a follow-on to the first find_the_stack problem from ACSC5. This was originally supposed to be the third one in a series of challenges based on this problem but I had some problems with number two so this became number two.
find_the_stack
This is the first of what will hopefully be many walk-throughs from various CTF competitions I’ve competed/worked on. This first challenge is a simple one that I created for the 5th annual Army Cyber Skills Challenge.