One thing that I first noticed occasionally as a Net Tech, and then more as an OC/T at NTC and finally a ton now that I have moved into the cyber side of the world is the just how important logs can be. The problem….we suck at actually saving the stupid things.
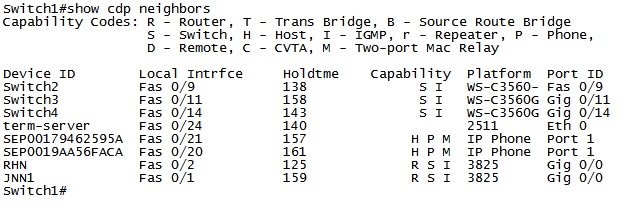
Cisco Discovery Protocol (CDP)
When there is a problem with the network, time matters. We need to be able to quickly move from device to device in order to identify and rectify the problem. In order for this to occur, we have to know where to go to next, and how to get there.
It’s all about that base(line)
Do you know what your baseline configuration is? Is it the same thing that you received on a CD from General Dynamics years ago or have you updated it over time as you have worked to refine and secure your network? If you do have a baseline, is it something that routinely roll-back to after each mission or do we just keep try to update the configurations each time we get a new message?
Security Technical Implementation Guide (STIG)
Many Net Techs have heard of a STIG (Security Technical Implementation Guide) but most have never actually looked at them before. The STIG, combined with NSA guides are considered the “best practices” for information assurance within DOD systems. While there is nothing that says that your systems MUST be configured to their standards it is important to realize that by not configuring them in the recommended way means that you are accepting risk.
Standardizing the LAN
Tactical networks are an ever changing beast. Links come and go frequently as units maneuver across the battlefield. Likewise, the BCT Main is a mobile headquarters that needs to be able to quickly setup and tear down in order to move to the next location. Having a standardized LAN setup can greatly reduce the amount of time required to reestablish the Main each time it moves, and greatly aid in troubleshooting after it has been established.