For anyone who doesn’t know, Mandiant is large cyber security company that was bought by Fireeye. They grabbed a lot of attention by the cyber security community when in 2013, they publicly released a report that linked the Chinese military to attacks dating back to at least 2006 on over 141 organizations. Each year they release a report on cyber security trends that they observed during the previous year. Granted, the results are screwed because they are based only on incidents that they responded to, but they at least give a good overall picture of what is going on around the world.
Signal-Chief is Now “Secure”
You likely haven’t noticed yet, but if you look at the top corner of your browser, you should be seeing a little lock symbol up there for the first time (at least when you came to this site). For years now, Signal-Chief has been served up on straight HTTP. I was never really worried about it because there is no personal information on the site, and the only person who actually logged into it was me (and I use unique passwords on everything)
Translating Geek to Geek
Imagine this scenario…. “The first neutron passes the LD and engages enemy position. The enemy position is destroyed and the damage is extensive enough to cause an adjoining position to catch fire. When the ammunition in that adjoining position explodes it takes out another position…” Huh?
I Know Nothing….and am proud of it.
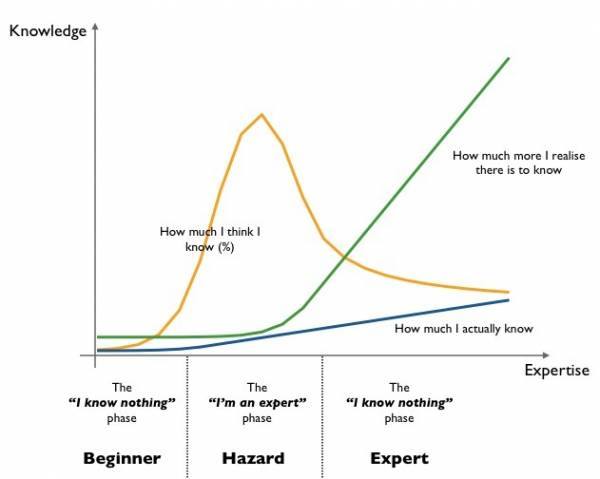
I was looking through Nixcraft on Facebook yesterday (if you haven’t been to it before, check it out) and came across the graph. As a warrant officer, we’re supposed to be experts in whatever field it is that we happen to be in. But what exactly does that mean?
Reflections from the NTC
In the 3 years, 4 months and 1 day since I arrived on Fort Irwin to being my job as the senior NETOPS trainer I can say that my perspective today compared to then has changed significantly. During that time I have worked on 26 rotations with 24 BCTs (2 of them twice), 21 Net Techs (3 of them twice) and way more signal Soldiers than I could possibly count. What follows are a number of final thoughts as I finish my time at the NTC.
But they didn’t teach me that in WOBC! – Comments in configs
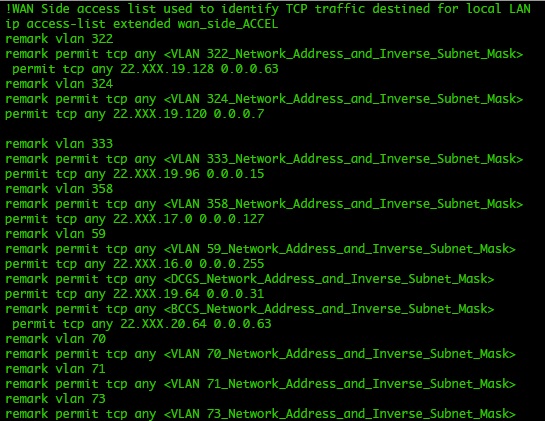
There are a few things that are in WIN-T that are not explained in school. You either find yourself figuring it out or being told by another Warrant. How many of you have noticed that there are configurations available for all your equipment in TXT format? How many of you use them to blow in configurations when replacing gear from your spares? How many of you have read all the comments?
Orders, Suggestions, and Good Ideas
Have you ever told a unit that you needed them to do something, only for them to completely blow you off? Since its formation, the Army has operated under as an organization of order. We as warrant officers have to learn to utilize the orders process to enable us to successfully manage the network.
Have you seen my image disk?
Imagine this. Your brigade is part of a Corps level task force preparing to move into an allied country to push out an invading Army. The unit has been on site for several weeks and is just waiting for the order to attack. One day you get a call from one of your battalions informing you that their SIPR call manager has crashed and that they will need to reimage the system. You reach into your box of CD/DVDs to find the call manager disks and discover that you don’t have it…..FML
JNN Team Integration
Do you have everyone that you need (or would like) to complete your mission? If you are like pretty much everyone in the Army, the answer to that question is no. Rarely does a unit have everyone assigned to it that they are authorized and even in the case that they do, you still have people pulling guard, on profile, or whatever. The short answer is that we never have enough people to take care of all of the tasks that need to be completed which is why it is critical that we effectively manage how we use our personnel.
It’s all about that base(line)
Do you know what your baseline configuration is? Is it the same thing that you received on a CD from General Dynamics years ago or have you updated it over time as you have worked to refine and secure your network? If you do have a baseline, is it something that routinely roll-back to after each mission or do we just keep try to update the configurations each time we get a new message?